SecureMySocial Issued 5th US Patent For Social Media Security Technology
Joseph Steinberg
DECEMBER 2, 2022
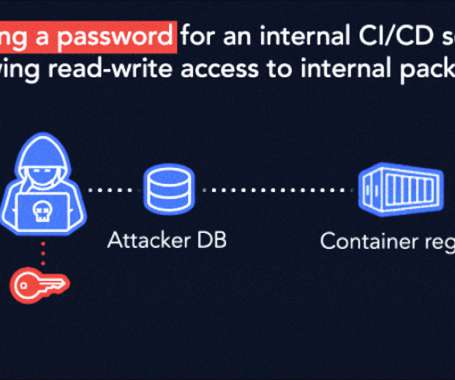
I am happy (and proud) to announce that SecureMySocial, a cybersecurity company that I co-founded, has been issued its fifth United States patent for social media security. The patent was issued by the United States Patent Office on September 6th, 2022, with a priority date going back over a decade, to June of 2012. Patent number US 11,438,334 entitled Systems and Methods for Securing Social Media for Users and Businesses and Rewarding for Enhancing Security , discloses a robust invention that a






































Let's personalize your content