Fooling a Voice Authentication System with an AI-Generated Voice
Schneier on Security
MARCH 1, 2023
A reporter used an AI synthesis of his own voice to fool the voice authentication system for Lloyd’s Bank.

Schneier on Security
MARCH 1, 2023
A reporter used an AI synthesis of his own voice to fool the voice authentication system for Lloyd’s Bank.

The Last Watchdog
MARCH 1, 2023
The IT world relies on digital authentication credentials, such as API keys, certificates, and tokens, to securely connect applications, services, and infrastructures. Related: The coming of agile cryptography These secrets work similarly to passwords, allowing systems to interact with one another. However, unlike passwords intended for a single user, secrets must be distributed.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Jane Frankland
MARCH 1, 2023
Around the world, people are gearing up to celebrate International Women’s Day on 8 March. But I have to ask the difficult question/s. Is it really something worth celebrating in cybersecurity? Have we really made enough progress that’s worthy of a celebration? Let’s be honest. Many believe the answer is no, and that we should be striking or boycotting the day instead.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

IT Security Guru
MARCH 1, 2023
Mobile phishing is an issue plaguing the masses and a growing concern for enterprises, particularly as 2022 had the highest percentage of mobile phishing encounter rates ever, according to Lookout ‘s Global State of Mobile Phishing report. On average, more than 30% of personal and enterprise users exposed to these attacks every quarter. In the U.K., there was a 35% increase in the average number of mobile devices exposed to at least one malicious phishing attack per quarter between 2020 a

CSO Magazine
MARCH 1, 2023
In 2022, I started a podcast aimed at converting more Gen Z to seek careers in cybersecurity. In doing so, I had to educate myself on what they value and realized the many differences between Gen Z and previous generations. Gen Z refers to those born between mid-to-late 1990s and 2010, making them between the ages of 11 and 28. This means they grew up experiencing a much faster rate in which technology evolves.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Trend Micro
MARCH 1, 2023
Find out how the Managed XDR team uncovered RedLine Stealer’s evasive spear-phishing campaign that targets the hospitality industry.

Graham Cluley
MARCH 1, 2023
Who has been warning Italian criminals that their phones are wiretapped? Can you trust your voice to protect your bank account? And why is TikTok being singled out by investigators? All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Dinah Davis.

Security Boulevard
MARCH 1, 2023
Software supply chain issues continue to be a concerning subject of late. Open source software (OSS) has many benefits, yet relying on many open source dependencies could cause security woes if it isn’t managed correctly. This problem has come into focus as more vulnerabilities present themselves and attacks on open source software ecosystems become more.

CSO Magazine
MARCH 1, 2023
Known vulnerabilities, compromise of legitimate package, and name confusion attacks are expected to be among the top ten open source software risks in 2023, according to a report by Endor Labs. The other major open source software risks, according to the report, include unmaintained software, outdated software, untracked dependencies, license risk, immature software, unapproved changes, and under/oversized dependency.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Boulevard
MARCH 1, 2023
Organizations worldwide store 60% of their data in the cloud. The popularity of cloud computing is undisputed in 2023 and is predicted to grow in future years. The main benefits of using cloud storage and computing services to run corporate virtual machines (VMs) include data availability and the cost-efficiency of such infrastructures. However, focusing on.

The Hacker News
MARCH 1, 2023
Six different law firms were targeted in January and February 2023 as part of two disparate threat campaigns distributing GootLoader and FakeUpdates (aka SocGholish) malware strains. GootLoader, active since late 2020, is a first-stage downloader that's capable of delivering a wide range of secondary payloads such as Cobalt Strike and ransomware.

CSO Magazine
MARCH 1, 2023
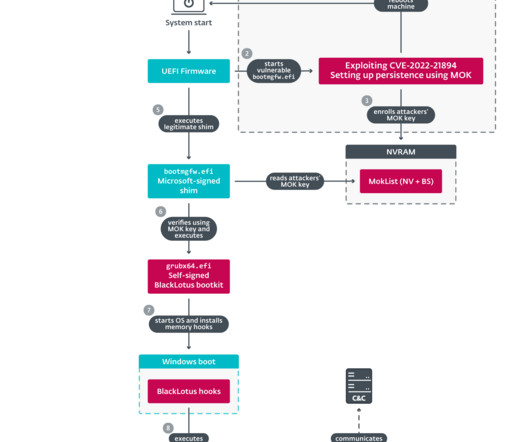
A Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus is found to be capable of bypassing an essential platform security feature, UEFI Secure Boot , according to researchers from Slovakia-based cybersecurity firm ESET. BlackLotus uses an old vulnerability and can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled, the researchers found.
SecureWorld News
MARCH 1, 2023
When it comes to cybersecurity, the use of automatic protection tools is half the battle. The human element plays an increasingly important role, as well, and for good reason. Scammers like to take shortcuts and know that it's easier to hoodwink people than it is to exploit software or hardware. Any organization with a well-guarded security perimeter is low-hanging fruit as long as its employees fall for phishing hoaxes.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Dark Reading
MARCH 1, 2023
The flaw, which drew attention in October when it was found in ConnectWise products, could pose a significant risk to the supply chain if not patched immediately.

Security Boulevard
MARCH 1, 2023
Federal agencies have 30 days to remove the popular Chinese social media app TikTok from federal government devices, according to a guidance memorandum issued by the White House. The memo, written by Office of Management and Budget director Shalanda Young and first seen and reported on by Reuters, applies to all federal agencies as well. The post White House Bans TikTok on Federal Devices appeared first on Security Boulevard.

Heimadal Security
MARCH 1, 2023
As a result of another attack on LastPass’s systems, the company disclosed a severe data breach in December 2022 that allowed threat actors to access encrypted password vaults. DevOps engineers’ home computers were breached and infected with a keylogger as part of a sustained cyber attack that exfiltrated sensitive data from Amazon AWS’s cloud storage […] The post LastPass Confirms Second Data Breach of Encrypted Password Vaults appeared first on Heimdal Security Blog.

Bleeping Computer
MARCH 1, 2023
When attempting to access Twitter's website, users see "Welcome to Twitter!" on the timeline. The alert, typically used for new signups, says, "Twitter is the best place to see what's happening in your world", with a Let's go button that lets you follow some people and topics. [.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.
Google Security
MARCH 1, 2023
Posted by Kiran Nair, Product Manager, Chrome Browser 1. Bring Chrome under Cloud Management Your journey towards keeping your Google Workspace users and data safe, starts with bringing your Chrome browsers under Cloud Management at no additional cost. Chrome Browser Cloud Management is a single destination for applying Chrome Browser policies and security controls across Windows, Mac, Linux, iOS and Android.
Bleeping Computer
MARCH 1, 2023
Microsoft has added two new utilities to the open-source PowerToys toolset to help Windows users paste text without formatting and make it easier to move the mouse across multiple screens or on ultra-wide monitors. [.

Heimadal Security
MARCH 1, 2023
Wondering what is crypto-ransomware? You’ve come to the right place. Because of the cryptocurrency boom, cyber threat actors have begun to use unauthorized and illegal methods to obtain cryptocurrencies. While ransomware typically demands Bitcoin as a ransom to ‘unblock’ access to systems/files, crypto-ransomware attacks are designed to mine cryptocurrencies without the users’ knowledge.

Bleeping Computer
MARCH 1, 2023
Aruba Networks published a security advisory to inform customers about six critical-severity vulnerabilities impacting multiple versions of ArubaOS, its proprietary network operating system. [.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

CompTIA on Cybersecurity
MARCH 1, 2023
Vlad Serov, a high school senior, has already earned five CompTIA certifications. See how his high school’s Cyber Lab program set him up for success.

Bleeping Computer
MARCH 1, 2023
Cisco has addressed a critical security vulnerability found in the Web UI of multiple IP Phone models that unauthenticated and remote attackers can exploit in remote code execution (RCE) attacks. [.

CyberSecurity Insiders
MARCH 1, 2023
From early this year, two malware variants targeted almost 6-7 law firms spread through two separate incidents, alerting whole of the world about the lurking cyber threat. Cybersecurity firm eSentire was the first to uncover the truth as its security analysts discovered that the two malicious software named GootLoader and SoCGholish were only infecting the servers used by employees of reputed law firms.

Security Boulevard
MARCH 1, 2023
LastPass has followed news of last month’s breach with details on a second attack in which developers were phished for their credentials. In the January incident, the password manager’s parent, GoTo, said that in addition to stealing encrypted backups containing customer data, hackers nicked an encryption key last November. “An unauthorized party gained access to.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

The Hacker News
MARCH 1, 2023
Google has announced the general availability of client-side encryption (CSE) for Gmail and Calendar, months after piloting the feature in late 2022. The data privacy controls enable "even more organizations to become arbiters of their own data and the sole party deciding who has access to it," Google's Ganesh Chilakapati and Andy Wen said.
Security Affairs
MARCH 1, 2023
ESET discovered a stealthy Unified Extensible Firmware Interface (UEFI) bootkit dubbed BlackLotus that is able to bypass the Secure Boot on Windows 11. Researchers from ESET discovered a new stealthy Unified Extensible Firmware Interface ( UEFI ) bootkit, named BlackLotus , that is able to bypass Secure Boot on Windows 11. Secure Boot is a security feature of the latest Unified Extensible Firmware Interface (UEFI) 2.3.1 designed to detect tampering with boot loaders, key operating system files,

Malwarebytes
MARCH 1, 2023
Voice ID is slowly rolling out across various banks worldwide as a way to perform user authentication over the phone. However, questions remain about just how secure it is. Now that we have freely available artificial intelligence (AI) happily replicating people’s voices, could it be a security risk? Some recent research suggests that it could.
Security Affairs
MARCH 1, 2023
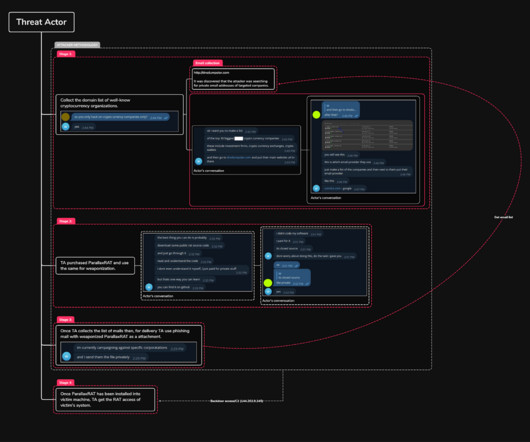
Experts warn of a new wave of attacks against cryptocurrency entities, threat actors are using a RAT dubbed Parallax RAT for Infiltration. Researchers from cybersecurity firm Uptycs warns of attacks targeting cryptocurrency organizations with the Parallax remote access Trojan (RAT). Parallax RAT has been distributed through malvertising and phishing campaigns since December 2019.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content