As Long as We’re on the Subject of CAPTCHAs
Schneier on Security
DECEMBER 16, 2022
There are these.

Graham Cluley
DECEMBER 16, 2022
Celebrated crime author Ann Cleeves turned to Twitter this week, desperate for help. The reason? The author, whose novels had been the inspiration for TV series like "Vera", had lost her HP laptop during a blizzard in Shetland.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
DECEMBER 16, 2022
The most recent iPhone update—to version 16.1.2—patches a zero-day vulnerability that “may have been actively exploited against versions of iOS released before iOS 15.1.” News : Apple said security researchers at Google’s Threat Analysis Group, which investigates nation state-backed spyware, hacking and cyberattacks, discovered and reported the WebKit bug.

Security Boulevard
DECEMBER 16, 2022
Around 50 so-called “booter” DDoS sites have been nuked by international law enforcement. And seven of their alleged administrators have been charged. The post Operation PowerOFF: DDoS Sites Denied Service (by US, UK, Europol) appeared first on Security Boulevard.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Heimadal Security
DECEMBER 16, 2022
This week, the Gemini cryptocurrency exchange disclosed that after a threat actor obtained the clients’ data from a third-party vendor, they became the victim of phishing attacks. BleepingComputer identified multiple posts on hacker forums offering to sell a database allegedly from Gemini containing email addresses, phone numbers, and other personal data of 5.7 million users. […].

SecureBlitz
DECEMBER 16, 2022
Today, we will answer the question – when is hacking illegal and legal? Before we jump into the topic about when hacking is considered illegal and when it is considered legal, let’s try to understand what hacking is. What Is Hacking? There are many ways in which the process of hacking could be explained. It […]. The post When Is Hacking Illegal And Legal?
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

SecureBlitz
DECEMBER 16, 2022
In this post, we will show you how to use our very own SecureBlitz Strong Password Generator. A completely free online password generator for internet users. It is no longer news that cybercriminals have doubled, and are wreaking havoc all over the world, cybersecurity experts and researchers reel out periodic findings on cyber-attacks week after […].

Heimadal Security
DECEMBER 16, 2022
Authorities from the Southern District of Texas accused eight men of committing securities fraud by participating in a “pump and dump” scheme. The scammers were running the fraud scheme on social media and managed to earn $114 million before they were discovered. How the “Pump and Dump” Scheme Worked The eight men used social media […]. The post 8 Social Media Influencers Accused of Securities Fraud in the US appeared first on Heimdal Security Blog.
Security Boulevard
DECEMBER 16, 2022
As we wrap up a year marked by a global pandemic, a protracted war in Ukraine, soaring inflation, exorbitant gas prices, and relentless ransomware attacks, we nevertheless look to 2023 in cybersecurity with a bit of hopefulness. Why? Because the drum beat for Collective Defense is gaining momentum across the public and private sectors. What's more, IronNet has launched a proactive threat intelligence feed called IronRadar SM that detects and blocks malicious command and control (C2) infrastructu

Cisco Security
DECEMBER 16, 2022
Attackers specifically craft business email compromise (BEC) and phishing emails using a combination of malicious techniques, expertly selected from an ever-evolving bag of tricks. They’ll use these techniques to impersonate a person or business that’s well-known to the targeted recipient and hide their true intentions, while attempting to avoid detection by security controls.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.
The Hacker News
DECEMBER 16, 2022
GitHub on Thursday said it is making available its secret scanning service to all public repositories on the code hosting platform for free. "Secret scanning alerts notify you directly about leaked secrets in your code," the company said, adding it's expected to complete the rollout by the end of January 2023.

Bleeping Computer
DECEMBER 16, 2022
Microsoft announced today that a future Microsoft Edge update would permanently disable the Internet Explorer 11 desktop web browser on some Windows 10 systems in February. [.].

Malwarebytes
DECEMBER 16, 2022
Apple has released new security content for iOS 16.1.2 and Safari 16.2. Normally we would say that Apple pushed out updates, but in this mysterious case the advisory is about an iPhone software update Apple released two weeks ago. As it turns out, to fix a zero-day security vulnerability that was actively exploited. Mitigation. The updates should all have reached you in your regular update routines, but it doesn't hurt to check if your device is at the latest update level.

Security Affairs
DECEMBER 16, 2022
An ex Twitter employee has been sentenced to three-and-a-half years in prison for spying on individuals on behalf of Saudi Arabia. On august 2022, the former Twitter employee, Ahmad Abouammo (44), was found guilty of gathering private information of certain Twitter users and passing them to Saudi Arabia. Now Abouammo was has been sentenced to three-and-a-half years in prison for spying on individuals on behalf of Saudi Arabia. “A California man was sentenced yesterday to 42 months in fed

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Boulevard
DECEMBER 16, 2022
The way MSPs target prospects has evolved. Using a one-size-fits-all approach is no longer the most effective option for MSPs. Read More. The post Top Three Tips for Building Your MSP Audience appeared first on Kaseya. The post Top Three Tips for Building Your MSP Audience appeared first on Security Boulevard.
Security Affairs
DECEMBER 16, 2022
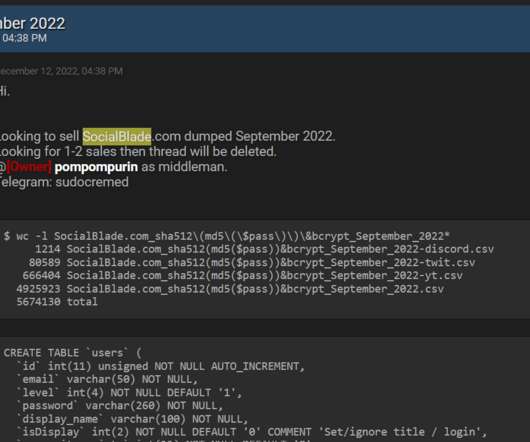
Social media analytics service Social Blade disclosed a security breach after a database containing allegedly stolen data from the company was offered for sale. Social Blade is an American social media analytics platform, the company disclosed the security breach after a database containing company data was offered for sale on a hacker forum this week.

Malwarebytes
DECEMBER 16, 2022
Warnings abound of a major new piece of fraud doing the rounds which uses your relative’s voice as part of a blackmail scam. What happens is the victim receives a call from said relative’s number, and they’re cut off by blackmailers who have them held hostage. The only way to get them back safely is to pay a sizable sum of money, usually within a time limit.
Security Affairs
DECEMBER 16, 2022
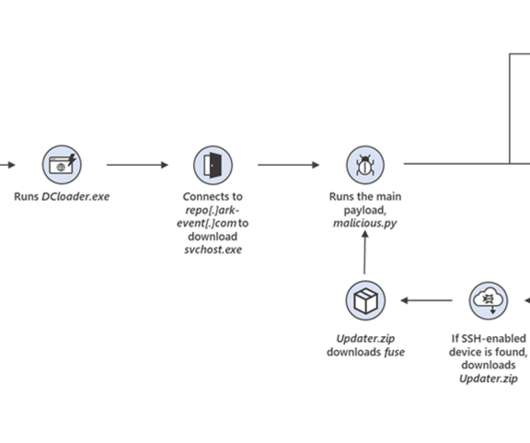
Microsoft announced that a botnet dubbed MCCrash is launching distributed denial-of-service (DDoS) attacks against private Minecraft servers. Microsoft spotted a cross-platform botnet, tracked as MCCrash, which has been designed to launch distributed denial-of-service (DDoS) attacks against private Minecraft servers. The IT giant tracks this cluster of activity as DEV-1028.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Heimadal Security
DECEMBER 16, 2022
On Thursday, Microsoft warned users about a cross-platform botnet that targets private Minecraft servers with distributed denial-of-service (DDoS) attacks. The botnet, known as MCCrash, has a special technique for propagating that allows it to infect Linux-based computers despite its origins in malicious software downloaded on Windows hosts. Cybersecurity researchers from Microsoft are tracking the cluster of […].

Security Affairs
DECEMBER 16, 2022
US CISA added two vulnerabilities impacting Veeam Backup & Replication software to its Known Exploited Vulnerabilities Catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added two vulnerabilities impacting Veeam Backup & Replication software, tracked as CVE-2022-26500 and CVE-2022-26501 (CVSS 3.1 Base Score 9.8), to its Known Exploited Vulnerabilities Catalog.

Heimadal Security
DECEMBER 16, 2022
Phishing scams have become more complex over time, and scammers are finding new ways to obtain information about their victims. This new phishing campaign is no different. The crook hides text in the Facebook posts to trick potential victims into giving up their account credentials and personally identifiable information. A malicious email impersonating Facebook’s copyright […].

Security Affairs
DECEMBER 16, 2022
Gemini crypto exchange warns users of an ongoing phishing campaign after a third-party vendor suffered a security breach. Gemini crypto exchange is warning of phishing campaigns targeting its users after a threat actor obtained their data by breaching a third-party vendor. The company pointed out that its systems were not impacted. “Some Gemini customers have recently been the target of phishing campaigns that we believe are the result of an incident at a third-party vendor.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Hacker News
DECEMBER 16, 2022
A former Twitter employee who was found guilty of spying on behalf of Saudi Arabia by sharing data pertaining to specific individuals has been sentenced to three-and-a-half years in prison. Ahmad Abouammo, 45, was convicted earlier this August on various criminal counts, including money laundering, fraud, falsifying records, and being an illegal agent of a foreign government.
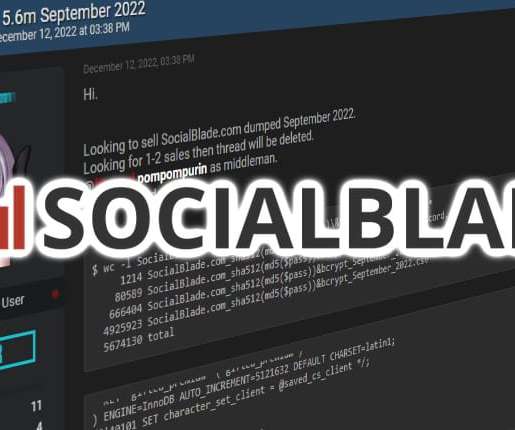
Graham Cluley
DECEMBER 16, 2022
Social media analytics service Social Blade has confirmed that it is investigating a security breach, after a hacker offered its user database for sale on an underground criminal website. Read more in my article on the Hot for Security blog.

Security Boulevard
DECEMBER 16, 2022
Insight #1. ". Lobbying from ITIC has pushed back on the recent OMB 22-18 directive to require self-attestations and SBOMs from software vendors selling to the US Government. It’s time we all start being more transparent about our secure software development processes and stop delaying the inevitable.". . Insight #2. ". Multiple state governments have banned TikTok on state-owned devices over the past few weeks due to concerns over how data has been managed.

Heimadal Security
DECEMBER 16, 2022
Ukrainian government networks were infected via trojanized ISO files posing as legitimate Windows 10 installers and several governmental institutions were hacked. Threat actors used malware to collect data from their victims, deploy additional malicious tools, and exfiltrate stolen data to controlled servers. According to cyber researchers, one of the malicious ISOs was hosted on the […].

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Boulevard
DECEMBER 16, 2022
As an eventful 2022 draws to a close, it’s worth analyzing and understanding the challenges organizations will be facing in the new year. This becomes even more imperative as the ever-changing cybersecurity landscape continues to evolve, often resembling a game of cat-and-mouse, where organizations and attackers compete to outwit one another. From bad bots to […].

Malwarebytes
DECEMBER 16, 2022
Criminals making use of booter services which execute Distributed Denial of Service (DDoS) attacks to take down websites will have to try a little bit harder today: A major international operation has taken no fewer than 48 of the most popular booter services offline. The operation, known as “Power Off,” included law enforcement agencies from the UK, the US, the Netherlands, Germany, and Poland.

The Hacker News
DECEMBER 16, 2022
Samba has released software updates to remediate multiple vulnerabilities that, if successfully exploited, could allow an attacker to take control of affected systems. The high-severity flaws, tracked as CVE-2022-38023, CVE-2022-37966, CVE-2022-37967, and CVE-2022-45141, have been patched in versions 4.17.4, 4.16.8 and 4.15.13 released on December 15, 2022.

Malwarebytes
DECEMBER 16, 2022
InfraGard, a partnership between the FBI and members of the private sector that was established to protect critical infrastructure in the US, has been infiltrated by a cybercriminal. As a result, its database of contact information is now for sale on an English-language cybercrime forum. InfraGard. InfraGard is a partnership between the Federal Bureau of Investigation (FBI) and members of the private sector that was created to help protect US critical infrastructure.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content