Why Your Enterprise Needs FIDO Authentication Technology
Lohrman on Security
APRIL 3, 2022
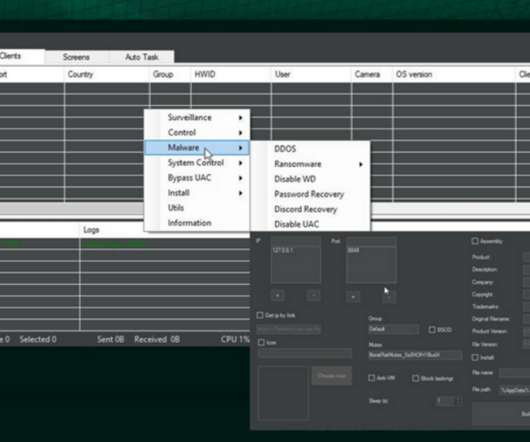
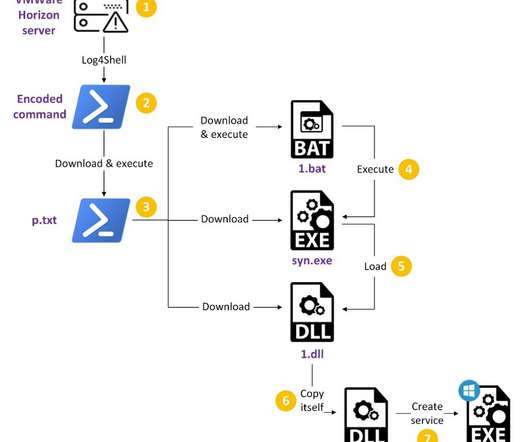
The Fast Identity Online Alliance (FIDO) offers a growing list of ways to authenticate users with a goal of reducing passwords. But why is it needed? How does it work? Where is this technology heading?






























Let's personalize your content