What Happened to Facebook, Instagram, & WhatsApp?
Krebs on Security
OCTOBER 4, 2021
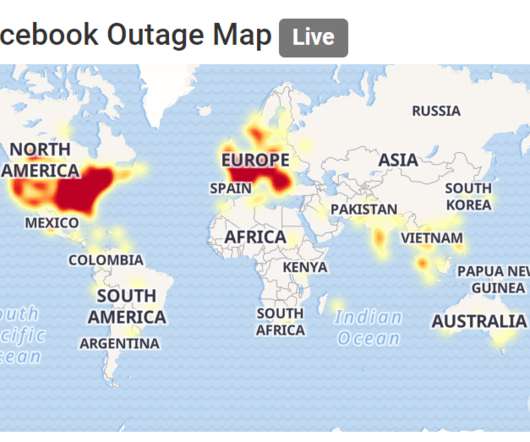
Facebook and its sister properties Instagram and WhatsApp are suffering from ongoing, global outages. We don’t yet know why this happened, but the how is clear: Earlier this morning, something inside Facebook caused the company to revoke key digital records that tell computers and other Internet-enabled devices how to find these destinations online.








































Let's personalize your content