Book Review: Cybersecurity Threats, Malware Trends and Strategies
Lohrman on Security
JULY 30, 2023
If you are looking for a deep-dive strategy book that looks into a wide range of cybersecurity topics in an updated fashion, this book is for you.

Lohrman on Security
JULY 30, 2023
If you are looking for a deep-dive strategy book that looks into a wide range of cybersecurity topics in an updated fashion, this book is for you.

Tech Republic Security
JULY 30, 2023
The Data Encryption Policy’s purpose is to define for employees, computer users and IT department staff the encryption requirements to be used on all computer, device, desktop, laptop, server, network storage and storage area network disks, and drives that access or store organization information to prevent unauthorized access to organization communications, email, records, files, databases,
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Boulevard
JULY 30, 2023
If you are looking for a deep-dive strategy book that looks into a wide range of cybersecurity topics in an updated fashion, this book is for you. The post Book Review: Cybersecurity Threats, Malware Trends and Strategies appeared first on Security Boulevard.

Tech Republic Security
JULY 30, 2023
It’s important to maintain accurate infrastructure inventories to assist secure and effective network administration. A checklist, like the accompanying file from TechRepublic Premium, is an easy and efficient way to begin the process of maintaining accurate infrastructure inventories. From the checklist: DON’T FORGET ABOUT FORGOTTEN SYSTEMS It’s common for technical network audits to surface forgotten.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

The Hacker News
JULY 30, 2023
Multiple security vulnerabilities have been disclosed in the Ninja Forms plugin for WordPress that could be exploited by threat actors to escalate privileges and steal sensitive data. The flaws, tracked as CVE-2023-37979, CVE-2023-38386, and CVE-2023-38393, impact versions 3.6.25 and below, Patchstack said in a report last week. Ninja Forms is installed on over 800,000 sites.

Security Affairs
JULY 30, 2023
Software firm Ivanti disclosed another security vulnerability impacting Endpoint Manager Mobile (EPMM), that it said actively exploited. Ivanti disclosed a new security vulnerability impacting Endpoint Manager Mobile (EPMM), tracked as CVE-2023-35081 (CVSS score: 7.8), that was exploited in the wild as part of an exploit chain by threat actors. “A vulnerability has been discovered in Ivanti Endpoint Manager Mobile (EPMM), formerly known as MobileIron Core.” reads the advisory publish
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Malwarebytes
JULY 30, 2023
The Cybersecurity and Infrastructure Security Agency (CISA) has published three malware analysis reports based on malware variants associated with the exploitation of a known vulnerability in Barracuda ESG appliances. The Common Vulnerabilities and Exposures (CVE) database lists publicly disclosed computer security flaws. The vulnerability at hand is listed as CVE-2023-2868 , which has a CVSS score 9.4 out of 10.
Security Affairs
JULY 30, 2023
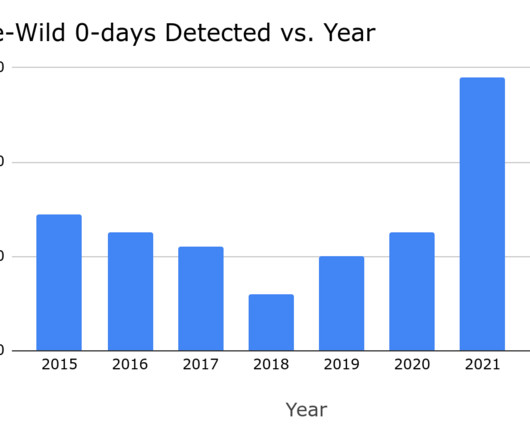
Google’s Threat Analysis Group Google states that more than 40% of zero-day flaws discovered in 2022 were variants of previous issues. The popular Threat Analysis Group (TAG) Maddie Stone wrote Google’s fourth annual year-in-review of zero-day flaws exploited in-the-wild [ 2021 , 2020 , 2019 ], it is built off of the mid-year 2022 review. In 2022, the researchers disclosed 41 actively exploited zero-day flaws, which marks the second-most ever recorded since we began tracking in mid-2014.
Malwarebytes
JULY 30, 2023
Last week on Malwarebytes Labs: Zimbra issues awaited patch for actively exploited vulnerability Patch now! Ivanti Endpoint Manager Mobile Authentication vulnerability used in the wild 60,000 Androids have stalkerware-type app Spyhide installed Ransomware groups claim responsibility for double-attack on Yamaha Update now! Apple fixes several serious vulnerabilities How to set up computer security for your parents Tampa General Hospital half thwarts ransomware attack, but still loses patient data

Security Affairs
JULY 30, 2023
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Now Abyss Locker also targets VMware ESXi servers Russian APT BlueBravo targets diplomatic entities with GraphicalProton backdoor CoinsPaid blames North Korea-linked APT Lazarus for theft of $37M worth of cryptocurrency Monitor Insider Threats but

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
Bleeping Computer
JULY 30, 2023
Microsoft has quietly announced an enhancement to the Edge browser's dark mode, making it even darker.

Security Boulevard
JULY 30, 2023
Thanks are in order to BSides Leeds for publishing their presenter’s outstanding BSides Leeds 2023 security content on the organizations’ YouTube channel. Permalink The post BSides Leeds 2023 – Alex Martin – Five Days, One Red Team, A Beach Like No Other: The Bank Job appeared first on Security Boulevard.

Bleeping Computer
JULY 30, 2023
Website of Israel's largest oil refinery operator, BAZAN Group is inaccessible from most parts of the world as threat actors claim to have hacked the Group's cyber systems. [.

Security Boulevard
JULY 30, 2023
In this episode, we explore the implications and ethical dilemmas of immortality in the digital world. Listen to our discussion about this cutting-edge technology and its potential impact on our privacy. Next, we discuss the growing trend of Apple and Google becoming custodians of our digital lives. Have these tech companies gone too far? Join […] The post Your Digital Immortality is Coming, Apple and Google Are Data Gatekeepers, Satellite Security Risks Revealed appeared first on Shared Securit

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Let's personalize your content