Joker malware infects over 500,000 Huawei Android devices
Bleeping Computer
APRIL 10, 2021
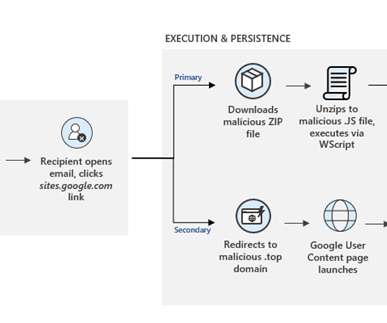
More than 500,000 Huawei users have downloaded from the company's official Android store applications infected with Joker malware that subscribes to premium mobile services. [.].
























Let's personalize your content