New Report on IoT Security
Schneier on Security
SEPTEMBER 27, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”
Schneier on Security
SEPTEMBER 27, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”

The Last Watchdog
SEPTEMBER 27, 2022
Digital resiliency has arisen as something of a Holy Grail in the current environment. Related: The big lesson of Log4j. Enterprises are racing to push their digital services out to the far edge of a highly interconnected, cloud-centric operating environment. This has triggered a seismic transition of company networks, one that has put IT teams and security teams under enormous pressure.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
SEPTEMBER 27, 2022
Initial reports suggest a basic security error allowed the attacker to access the company's live customer database via an unauthenticated API

The Hacker News
SEPTEMBER 27, 2022
WhatsApp has released security updates to address two flaws in its messaging app for Android and iOS that could lead to remote code execution on vulnerable devices.
Speaker: William Hord, Vice President of ERM Services
Join us as we discuss the various tangents of data and the change management process that will help you make better risk-based business decisions to save time and money for your organization.

Dark Reading
SEPTEMBER 27, 2022
SOC metrics will allow stakeholders to track the current state of a program and how it's supporting business objectives

Cisco CSR
SEPTEMBER 27, 2022
Explore the nature of vulnerabilities in this episode of ThreatWise TV. It’s shaping up to be another big year for vulnerability disclosure. Already the number of Common Vulnerabilities and Exposures (CVEs) disclosed has crossed 18,000 and it’s on track to make this another record-breaking year.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Boulevard
SEPTEMBER 27, 2022
The Ukrainian government has warned that Russia is planning a massive attack against the critical infrastructure of Ukraine and of its allies. The post Russia ‘Plans’ HUGE Cyberattack on Critical Infrastructure appeared first on Security Boulevard.
Dark Reading
SEPTEMBER 27, 2022
This Tech Tip outlines three steps security teams should take to protect information stored in Salesforce

Cisco CSR
SEPTEMBER 27, 2022
Written by Martin Lee and Richard Archdeacon.

Dark Reading
SEPTEMBER 27, 2022
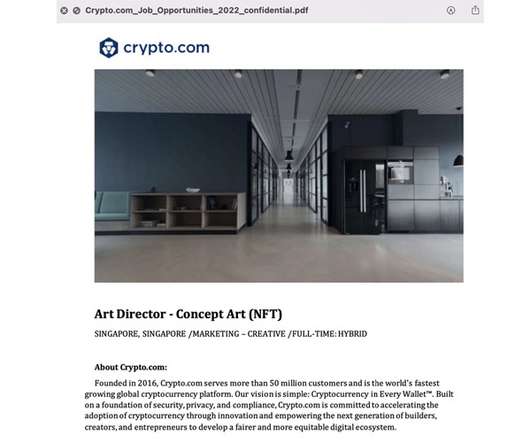
Previously observed using fake Coinbase jobs, the North Korea-sponsored APT has expanded into using Crypo.com gigs as cover to distribute malware

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
In this webinar, Ronald Eddings, Cybersecurity Expert, will outline the relationship between SaaS apps and IT & security teams, along with several actionable solutions to overcome the new difficulties facing your organization.

WIRED Threat Level
SEPTEMBER 27, 2022
Pornhub is trialing a new automated tool that pushes CSAM-searchers to seek help for their online behavior. Will it work? Security Security / Privacy

Dark Reading
SEPTEMBER 27, 2022
Why cyber teams are now front and center for business enablement within organizations, and the significant challenges they face
Tech Republic Security
SEPTEMBER 27, 2022
Microsoft investigated a new kind of attack where malicious OAuth applications were deployed on compromised cloud tenants before being used for mass spamming. The post Malicious Oauth app enables attackers to send spam through corporate cloud tenants appeared first on TechRepublic.

Dark Reading
SEPTEMBER 27, 2022
There are numerous strategies to lessen the possibility and effects of a cyberattack, but doing so takes careful planning and targeted action

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Through a detailed analysis of major attacks and their consequences, Karl Camilleri, Cloud Services Product Manager at phoenixNAP, will discuss the state of ransomware and future predictions, as well as provide best practices for attack prevention and recovery.
WIRED Threat Level
SEPTEMBER 27, 2022
The fun-loving cybercriminals blamed for breaches of Uber and Rockstar are exposing weaknesses in ways others aren't. Security Security / Cyberattacks and Hacks
Dark Reading
SEPTEMBER 27, 2022
Azure says cloud-native single sign-on with a passwordless option is most-requested new AVD feature in the product's history

SecureWorld News
SEPTEMBER 27, 2022
Harvard's Belfer Center for Science and International Affairs today released its updated 2022 National Cyber Power Index (NCPI), a follow-up to its groundbreaking 2020 index that ranks 30 countries according to their capability and intent to pursue eight objectives of cyber power.

Dark Reading
SEPTEMBER 27, 2022
TCP-based, DNS water-torture, and carpet-bombing attacks dominate the DDoS threat landscape, while Ireland, India, Taiwan, and Finland are battered by DDoS attacks resulting from the Russia/Ukraine war

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance
Security Affairs
SEPTEMBER 27, 2022
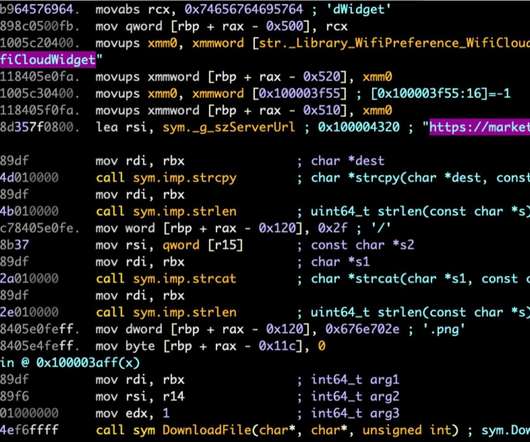
North Korea-linked Lazarus APT group is targeting macOS Users searching for jobs in the cryptocurrency industry. North Korea-linked Lazarus APT group continues to target macOS with a malware campaign using job opportunities as a lure.

Dark Reading
SEPTEMBER 27, 2022
Using its "Exmatter" tool to corrupt rather than encrypt files signals a new direction for financially motivated cybercrime activity, researchers say
Security Affairs
SEPTEMBER 27, 2022
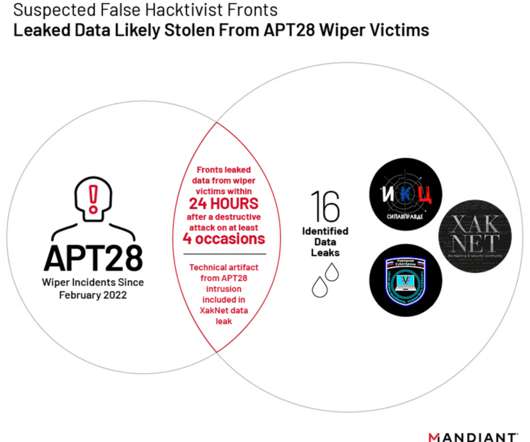
Researchers are tracking multiple self-proclaimed hacktivist groups working in support of Russia, and identified 3 groups linked to the GRU.
The Hacker News
SEPTEMBER 27, 2022
As many as 75 apps on Google Play and 10 on Apple App Store have been discovered engaging in ad fraud as part of an ongoing campaign that commenced in 2019.

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.

Security Affairs
SEPTEMBER 27, 2022
Elbit Systems of America, a subsidiary of defense giant Elbit Systems, disclosed a data breach after Black Basta ransomware gang claimed to have hacked it.
Security Boulevard
SEPTEMBER 27, 2022
Netography today added support for context labels and tagging to a software-as-a-service (SaaS) platform that provides deep packet inspection capabilities to identify cybersecurity threats in near-real-time.

Security Affairs
SEPTEMBER 27, 2022
WhatsApp has addressed two severe Remote Code Execution vulnerabilities affecting the mobile version of the software.
The Hacker News
SEPTEMBER 27, 2022
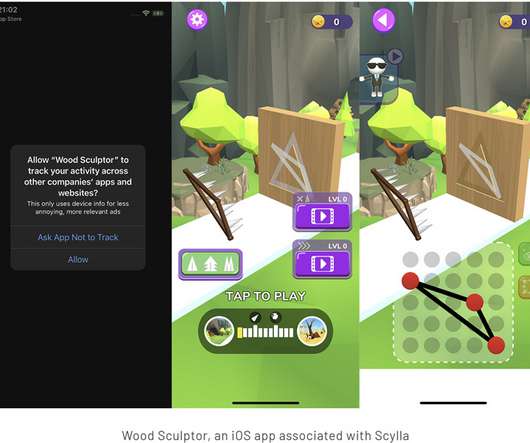
The infamous Lazarus Group has continued its pattern of leveraging unsolicited job opportunities to deploy malware targeting Apple's macOS operating system.
SecureBlitz
SEPTEMBER 27, 2022
This post will show you why ISO 27001 is important for small businesses… Information security refers to the measures taken to keep data secure from unauthorized access or changes.
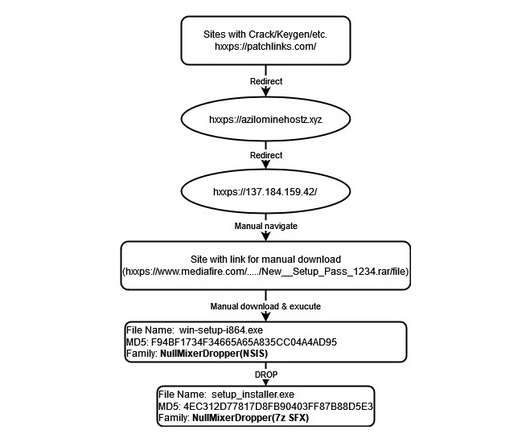
The Hacker News
SEPTEMBER 27, 2022
Cybercriminals are continuing to prey on users searching for cracked software by directing them to fraudulent websites hosting weaponized installers that deploy malware called NullMixer on compromised systems.
Security Affairs
SEPTEMBER 27, 2022
The recently discovered Erbium information-stealer is being distributed as fake cracks and cheats for popular video games.

The Hacker News
SEPTEMBER 27, 2022
The Ukrainian government on Monday warned of "massive cyberattacks" by Russia targeting critical infrastructure facilities located in the country and that of its allies.

CyberSecurity Insiders
SEPTEMBER 27, 2022
Russia launched a cyber attack on a private satellite operator called KA-SAT Network, just after it started an invasion of Ukraine 8 months ago.

Bleeping Computer
SEPTEMBER 27, 2022
Meta says it took down a large network of Facebook and Instagram accounts pushing disinformation published on more than 60 websites that spoofed multiple legitimate news sites across Europe. [.]. Security
Let's personalize your content