FTC’s Voice Cloning Challenge
Schneier on Security
NOVEMBER 16, 2023
The Federal Trade Commission is running a competition “to foster breakthrough ideas on preventing, monitoring, and evaluating malicious voice cloning.

Schneier on Security
NOVEMBER 16, 2023
The Federal Trade Commission is running a competition “to foster breakthrough ideas on preventing, monitoring, and evaluating malicious voice cloning.

Krebs on Security
NOVEMBER 16, 2023
Prosecutors in Finland this week commenced their criminal trial against Julius Kivimäki , a 26-year-old Finnish man charged with extorting a once popular and now-bankrupt online psychotherapy practice and thousands of its patients. In a 2,200-page report, Finnish authorities laid out how they connected the extortion spree to Kivimäki, a notorious hacker who was convicted in 2015 of perpetrating tens of thousands of cybercrimes, including data breaches, payment fraud, operating a botnet and calli
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

NetSpi Technical
NOVEMBER 16, 2023
As we were preparing our slides and tools for our DEF CON Cloud Village Talk ( What the Function: A Deep Dive into Azure Function App Security ), Thomas Elling and I stumbled onto an extension of some existing research that we disclosed on the NetSPI blog in March of 2023. We had started working on a function that could be added to a Linux container-based Function App to decrypt the container startup context that is passed to the container on startup.

Bleeping Computer
NOVEMBER 16, 2023
Toyota Financial Services (TFS) has confirmed that it detected unauthorized access on some of its systems in Europe and Africa after Medusa ransomware claimed an attack on the company. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
NOVEMBER 16, 2023
Samsung Electronics disclosed a data breach that exposed customer personal information to an unauthorized individual. Samsung Electronics suffered a data breach that exposed the personal information of some of its customers to an unauthorized individual. The security breach was discovered on November 13, 2023, and impacted customers who made purchases from the Samsung UK online store between July 1, 2019, and June 30, 2020.

Bleeping Computer
NOVEMBER 16, 2023
Fortinet is alerting customers of a critical OS command injection vulnerability in FortiSIEM report server that could be exploited by remote, unauthenticated attackers to execute commands through specially crafted API requests. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
NOVEMBER 16, 2023
The City of Long Beach in California is warning that they suffered a cyberattack on Tuesday that has led them to shut down portions of their IT network to prevent the attack's spread. [.

Malwarebytes
NOVEMBER 16, 2023
An alarm system company that allows those in need to ask for help at the touch of a button has suffered a cyberattack, causing serious disruption. Tunstall Netherlands says the attack left the control room struggling to receive distress calls from clients on Sunday November 12, 2023. Tunstall, among others, provides services and systems to allow smart monitoring in various healthcare settings.

Bleeping Computer
NOVEMBER 16, 2023
The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Security Agency released an advisory about the evasive threat actor tracked as Scattered Spider, a loosely knit hacking collective that now collaborates with the ALPHV/BlackCat Russian ransomware operation. [.

IT Security Guru
NOVEMBER 16, 2023
Artificial intelligence (AI) technology functions in a manner that helps ease human life. Through AI-enabled systems, different industries have been able to minimize human error and automate repetitive processes and tasks while smoothly handling big data. Unlike humans, who are productive only a few hours a day and need time off and breaks for a healthy work-life balance, AI can operate continuously without breaks, think faster, and handle multiple tasks simultaneously while delivering accurate

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
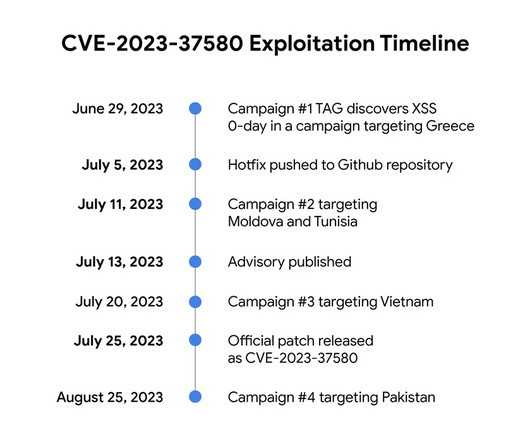
Security Affairs
NOVEMBER 16, 2023
Google TAG revealed that threat actors exploited a Zimbra Collaboration Suite zero-day ( CVE-2023-37580 ) to steal emails from governments. Google Threat Analysis Group (TAG) researchers revealed that a zero-day vulnerability, tracked as CVE-2023-37580 (CVSS score: 6.1), in the Zimbra Collaboration email software was exploited by four different threat actors to steal email data, user credentials, and authentication tokens from government organizations.

Bleeping Computer
NOVEMBER 16, 2023
MySQL servers are being targeted by the 'Ddostf' malware botnet to enslave them for a DDoS-as-a-Service platform whose firepower is rented to other cybercriminals. [.

WIRED Threat Level
NOVEMBER 16, 2023
Signal’s president reveals the cost of running the privacy-preserving platform—not just to drum up donations, but to call out the for-profit surveillance business models it competes against.

Security Boulevard
NOVEMBER 16, 2023
Experts explain how expanded cybersecurity regulation changes the CISO’s role, cyber liability insurance, and pathways to cyber resilience. The post Complying with Confidence: Navigating Cybersecurity Regulation and Legislation appeared first on SafeBreach. The post Complying with Confidence: Navigating Cybersecurity Regulation and Legislation appeared first on Security Boulevard.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
WIRED Threat Level
NOVEMBER 16, 2023
The National Telecommunication Monitoring Center in Bangladesh exposed a database to the open web. The types of data leaked online are extensive.

Security Boulevard
NOVEMBER 16, 2023
APIs have been with us since before they were called APIs. Application programming interfaces as an interface between software or between users and software have been around since the 1940’s, around 20 years before such interfaces were called APIs. In the past couple of decades, APIs have really come into their own with the proliferation […] The post The ABCs of API Security: A New (Free!

Dark Reading
NOVEMBER 16, 2023
More than half of organizations are nowhere near ditching passwords, even as cyberattackers continue to have a field day with workers' poor credential choices.

Security Boulevard
NOVEMBER 16, 2023
What the Alaska Purchase and Seward's Folly can teach us about the strategy and upside for Cisco's acquisition of Splunk. The post Cisco’s Cybersecurity Shopping Spree (Part 2) appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Dark Reading
NOVEMBER 16, 2023
There's no time to waste: For organizations on the fence about patching the critical bug in ActiveMQ, the new proof-of-concept exploit should push them towards action.

Security Boulevard
NOVEMBER 16, 2023
Google and Yahoo have recently announced new requirements. The post Google And Yahoo New Email Authentication Requirements appeared first on EasyDMARC. The post Google And Yahoo New Email Authentication Requirements appeared first on Security Boulevard.

Dark Reading
NOVEMBER 16, 2023
People are not robots; their decisions are based on emotion as much as data. Often, this can lead them to make mistakes with serious security implications for the business.

Security Boulevard
NOVEMBER 16, 2023
Microsoft just released its November Patch Tuesday security updates. In this latest installment, a total of 58 vulnerabilities have been addressed. Among these, the update tackles five zero-day vulnerabilities, with three actively exploited in the wild, warranting immediate attention and action from users and organizations alike. A detailed overview of these critical updates is provided below.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

The Hacker News
NOVEMBER 16, 2023
A zero-day flaw in the Zimbra Collaboration email software was exploited by four different groups in real-world attacks to pilfer email data, user credentials, and authentication tokens. "Most of this activity occurred after the initial fix became public on GitHub," Google Threat Analysis Group (TAG) said in a report shared with The Hacker News.
We Live Security
NOVEMBER 16, 2023
How much contact and personal information do you give away in your LinkedIn profile and who can see it? Here’s why less may be more.

The Hacker News
NOVEMBER 16, 2023
A hacking group that leveraged a recently disclosed security flaw in the WinRAR software as a zero-day has now been categorized as an entirely new advanced persistent threat (APT). Cybersecurity company NSFOCUS has described DarkCasino as an "economically motivated" actor that first came to light in 2021.

Bleeping Computer
NOVEMBER 16, 2023
Microsoft will roll out the Copilot AI-powered assistant to Windows 10 systems enrolled in the Insider Program over the coming months. [.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Heimadal Security
NOVEMBER 16, 2023
Today, the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) have jointly issued a warning about the Rhysida ransomware group. This gang has been attacking various organizations in different sectors since May 2023. A detailed Cybersecurity Advisory (CSA) has been released as part of the #StopRansomware initiative, highlighting the group’s methods and the risks […] The post FBI and CISA Issue Advisory on Rhysida Ransomware appeared first on Heimdal Security Blog.
Bleeping Computer
NOVEMBER 16, 2023
DDoS attacks are increasingly taking down even the largest tech companies. Learn more Specops Software on these types of attacks and how you can protect your devices from being recruited into botnets. [.
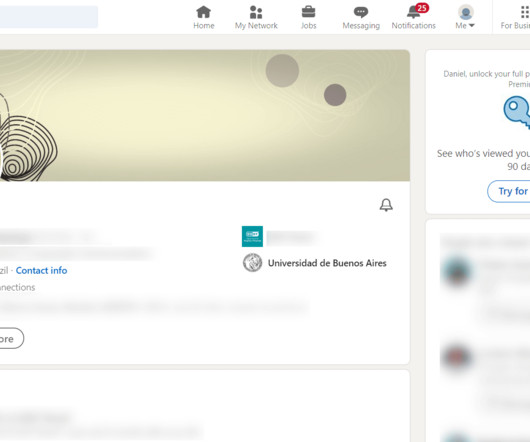
We Live Security
NOVEMBER 16, 2023
How much contact and personal information do you give away in your LinkedIn profile and who can see it? Here’s why less may be more.

The Hacker News
NOVEMBER 16, 2023
The threat actors behind the Rhysida ransomware engage in opportunistic attacks targeting organizations spanning various industry sectors. The advisory comes courtesy of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC).

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content