David Kahn
Schneier on Security
FEBRUARY 2, 2024
David Kahn has died. His groundbreaking book, The Codebreakers was the first serious book I read about codebreaking, and one of the primary reasons I entered this field. He will be missed.

Schneier on Security
FEBRUARY 2, 2024
David Kahn has died. His groundbreaking book, The Codebreakers was the first serious book I read about codebreaking, and one of the primary reasons I entered this field. He will be missed.

Tech Republic Security
FEBRUARY 2, 2024
The FBI spotted this state-sponsored attack that highlights how home office setups can be overlooked when it comes to employees’ cybersecurity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
FEBRUARY 2, 2024
AnyDesk confirmed today that it suffered a recent cyberattack that allowed hackers to gain access to the company's production systems. BleepingComputer has learned that source code and private code signing keys were stolen during the attack. [.

Security Affairs
FEBRUARY 2, 2024
Albania’s Institute of Statistics (INSTAT) announced that it was targeted by a sophisticated cyberattack that affected some of its systems. A sophisticated cyberattack on Wednesday hit Albania’s Institute of Statistics (INSTAT). The institute confirmed that the attack affected some of its systems. Albania’s Institute of Statistics (INSTAT) promptly activated emergency protocols to respond to the incident.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
FEBRUARY 2, 2024
Credential stuffing and harvesting, although similar, have nuanced differences particularly in how credentials are stolen, acquired and used. The post Credential Harvesting Vs. Credential Stuffing Attacks: What’s the Difference? appeared first on Security Boulevard.

eSecurity Planet
FEBRUARY 2, 2024
Within the last couple of months, smart device vulnerabilities have been piling up, prompting businesses to protect their Internet of Things (IoT) environments. But that doesn’t just include thermostats, printers, and other connected devices that you have to protect — it now means electric cars, too. Teslas have plenty of vulnerabilities, as cybersecurity researchers have recently discovered.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Graham Cluley
FEBRUARY 2, 2024
China-sponsored attacks likened to "placing bombs in water treatment facilities, and power plants". Is it just me, or does this sound like the plot of a Mission Impossible movie?

Security Boulevard
FEBRUARY 2, 2024
Most IT practitioners rely on legacy platforms and practices originally designed for on-premises IT to secure cloud computing environments. The post Survey Surfaces Raft of Cloud Security Challenges appeared first on Security Boulevard.

Bleeping Computer
FEBRUARY 2, 2024
Lurie Children's Hospital in Chicago was forced to take IT systems offline after a cyberattack, disrupting normal operations and delaying medical care in some instances. [.

Security Affairs
FEBRUARY 2, 2024
Cloudflare revealed that a nation-state actor breached its internal Atlassian server, gaining access to the internal wiki and its bug database (Atlassian Jira). The incident took place on Thanksgiving Day, November 23, 2023, and Cloudflare immediately began an investigation with the help of CrowdStrike. The company pointed out that no customer data or systems were impacted by this security breach.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Malwarebytes
FEBRUARY 2, 2024
In an emergency directive , the Cybersecurity and Infrastructure Security Agency (CISA) has ordered all federal agencies to disconnect all instances of Ivanti Connect Secure and Policy Secure solution products from agency networks no later than 11:59PM on Friday February 2, 2024. Besides the Ivanti vulnerabilities actively exploited in massive numbers we wrote about on January 11, 2024, alerts sounded about two new high severity flaws on January 31, 2024.
Security Affairs
FEBRUARY 2, 2024
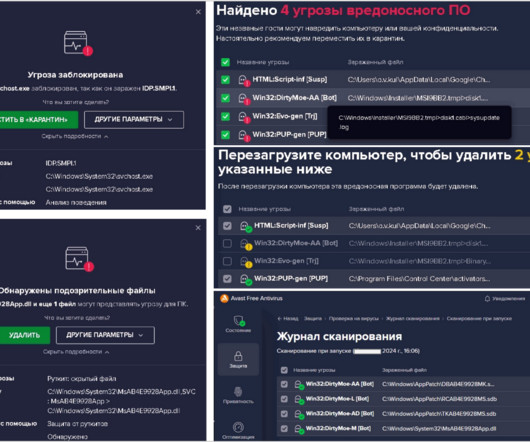
The Computer Emergency Response Team in Ukraine (CERT-UA) reported that a PurpleFox malware campaign had already infected at least 2,000 computers in the country. The Computer Emergency Response Team in Ukraine (CERT-UA) is warning about a malware campaign that has infected at least 2,000 computers in the country with the PurpleFox malware (aka ‘ DirtyMoe ‘). “The Government Computer Emergency Response Team of Ukraine CERT-UA, guided by Clause 1 of Article 9 of the Law of Ukrai

The Hacker News
FEBRUARY 2, 2024
Remote desktop software maker AnyDesk disclosed on Friday that it suffered a cyber attack that led to a compromise of its production systems. The German company said the incident, which it discovered following a security audit, is not a ransomware attack and that it has notified relevant authorities.

Security Affairs
FEBRUARY 2, 2024
A former software engineer with the U.S. CIA has been sentenced to 40 years in prison for leaking classified documents. Former CIA employee Joshua Adam Schulte has been sentenced to 40 years in prison for passing classified documents to WikiLeaks and for possessing child pornographic material. “Damian Williams, the United States Attorney for the Southern District of New York; Matthew G.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Bleeping Computer
FEBRUARY 2, 2024
Aliaksandr Klimenka, a Belarusian and Cypriot national, has been indicted in the U.S. for his involvement in an international cybercrime money laundering operation. [.
Security Affairs
FEBRUARY 2, 2024
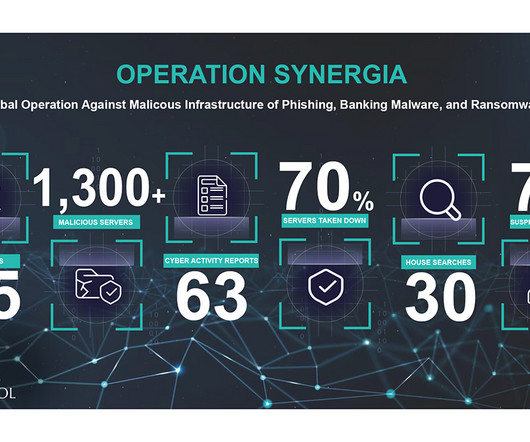
An international law enforcement operation, named Synergia, led to the arrest of 31 individuals involved in ransomware, banking malware, and phishing attacks. Operation Synergia was led by Interpol and ran from September to November 2023 involving law enforcement agencies from 50 countries. The international law enforcement operation was launched to curb the escalation and professionalisation of transnational cybercrime.

Security Boulevard
FEBRUARY 2, 2024
C# — Rust in peas: Microsoft 365 “Core Platform Substrate” gets rewrite in Rust language. The post Microsoft Ditches C# for Rust: M365 Core Gets Safety and Perf Boosts appeared first on Security Boulevard.

Graham Cluley
FEBRUARY 2, 2024
Data and software services firm Blackbaud's cybersecurity was criticised as "lax" and "shoddy" by the United States Federal Trade Commission (FTC) in a damning post-mortem of the business’s February 2020 data breach. Read more in my article on the Hot for Security blog.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Penetration Testing
FEBRUARY 2, 2024
A critical vulnerability in the decentralized social networking platform Mastodon could be exploited to impersonate and take over any remote account. Mastodon is a free, open-source social network server based on ActivityPub where users can... The post Mastodon Alert: CVE-2024-23832 Unlocks Account Takeover Threat appeared first on Penetration Testing.

The Hacker News
FEBRUARY 2, 2024
The decentralized social network Mastodon has disclosed a critical security flaw that enables malicious actors to impersonate and take over any account. "Due to insufficient origin validation in all Mastodon, attackers can impersonate and take over any remote account," the maintainers said in a terse advisory. The vulnerability, tracked as CVE-2024-23832, has a severity rating of 9.
Penetration Testing
FEBRUARY 2, 2024
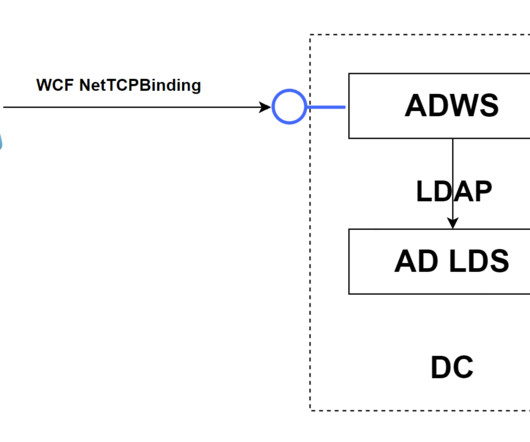
SOAPHound SOAPHound is a.NET data collector tool, which collects Active Directory data via the Active Directory Web Services (ADWS) protocol. SOAPHound is an alternative to several open-source security tools that are commonly used... The post SOAPHound: enumerate Active Directory environments via ADWS protocol appeared first on Penetration Testing.

Heimadal Security
FEBRUARY 2, 2024
Cloudflare disclosed a security breach today, revealing that a suspected nation-state attacker infiltrated its internal Atlassian server. The attack, which began on November 14, compromised Cloudflare’s Confluence wiki, Jira bug database, and Bitbucket source code management system. How did attackers first gain access to Cloudflare’s systems?

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Penetration Testing
FEBRUARY 2, 2024
AnyDesk, a widely used remote desktop software, recently announced a significant breach within its production environment. Despite the unsettling access gained by hackers, AnyDesk assured its user base that no authentication tokens were compromised,... The post AnyDesk’s Cybersecurity Breach: Unveiling the Recent Attack appeared first on Penetration Testing.

Bleeping Computer
FEBRUARY 2, 2024
Attacks on hospitals continued this week, with ransomware operations disrupting patient care as they force organization to respond to cyberattacks. [.

Security Boulevard
FEBRUARY 2, 2024
CEOs are becoming more hands-on and prioritizing cyber resilience as the traditional silos between ITOps and security teams break down. The post Security Leaders, C-Suite Unite to Tackle Cyberthreats appeared first on Security Boulevard.

SecureWorld News
FEBRUARY 2, 2024
Ransomware, as you know, is a big problem. In the last few years, this digital crime has largely harmed big organizations. But, ordinary people like us are now starting to take a lot more direct heat. For the last nine months, ordinary consumers, including parents and patients, have found themselves in the crosshairs of these cybercriminals. Let's paint a real-life picture here.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

The Hacker News
FEBRUARY 2, 2024
Russian state-sponsored actors have staged NT LAN Manager (NTLM) v2 hash relay attacks through various methods from April 2022 to November 2023, targeting high-value targets worldwide.

Penetration Testing
FEBRUARY 2, 2024
In the shadowy corners of the internet, an unending battle rages between cybersecurity defenders and nefarious cybercriminals. Recently, a detailed report from AhnLab Security Intelligence Center has shed light on the sophisticated strategies employed... The post Backdoor Breaches: The Rise of Stealthy Linux System Attacks appeared first on Penetration Testing.

The Hacker News
FEBRUARY 2, 2024
An INTERPOL-led collaborative operation targeting phishing, banking malware, and ransomware attacks has led to the identification of 1,300 suspicious IP addresses and URLs. The law enforcement effort, codenamed Synergia, took place between September and November 2023 in an attempt to blunt the "growth, escalation and professionalization of transnational cybercrime.

CompTIA on Cybersecurity
FEBRUARY 2, 2024
An English teacher with a tech background shares how she transitioned to a cybersecurity career with CompTIA Security+.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content