AutoSpill attack steals credentials from Android password managers
Bleeping Computer
DECEMBER 9, 2023
Security researchers developed a new attack, which they named AutoSpill, to steal account credentials on Android during the autofill operation. [.

Bleeping Computer
DECEMBER 9, 2023
Security researchers developed a new attack, which they named AutoSpill, to steal account credentials on Android during the autofill operation. [.
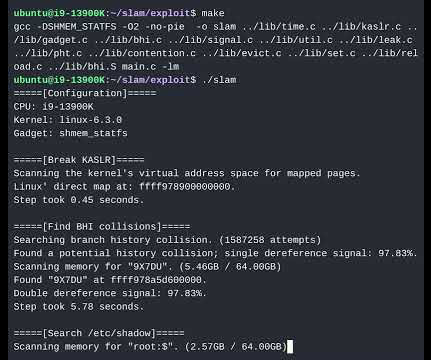
The Hacker News
DECEMBER 9, 2023
Researchers from the Vrije Universiteit Amsterdam have disclosed a new side-channel attack called SLAM that could be exploited to leak sensitive information from kernel memory on current and upcoming CPUs from Intel, AMD, and Arm.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
DECEMBER 9, 2023
Kentucky health system Norton Healthcare disclosed a data breach after it was a victim of a ransomware attack in May. Norton Healthcare disclosed a data breach after a ransomware attack that hit the organization on May 9, 2023. The security breach exposed personal information belonging to patients, employees, and dependents. The health system notified federal law enforcement and launched an investigation into the incident with the help of a leading forensic security provider.

Penetration Testing
DECEMBER 9, 2023
A critical security flaw was found in Elementor, a popular WordPress website builder plugin used by over 5 million websites worldwide. The vulnerability, identified as an ‘authenticated arbitrary file upload’ issue, was initially discovered... The post CVE-2023-48777: Critical Vulnerability in Elementor Affecting Over 5 Million Websites appeared first on Penetration Testing.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
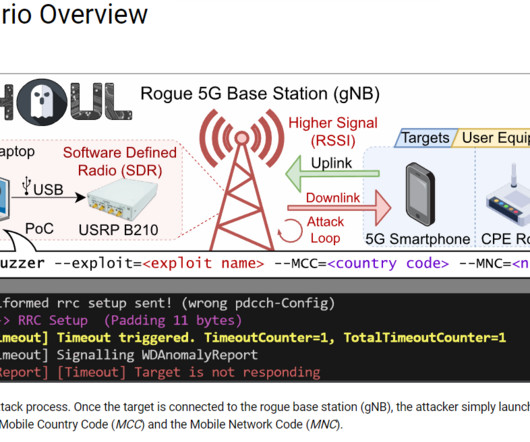
Security Affairs
DECEMBER 9, 2023
A set of flaws, collectively called 5Ghoul, in the firmware implementation of 5G mobile network modems from major vendors impacts Android and iOS devices. A team of researchers from the Singapore University of Technology and Design discovered a set of security vulnerabilities in the firmware implementation of 5G mobile network modems from major chipset vendors.

Security Boulevard
DECEMBER 9, 2023
Managing access rights for users has persistently posed a challenge for organizations, regardless of their size or industry. Access governance aims to enhance productivity while minimizing security risks. Additionally, maintaining a transparent overview of individuals with access to particular digital assets and ensuring the legitimacy of that access within compliance boundaries remains an obstacle.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
DECEMBER 9, 2023
Importance of Server Backup: Understanding the Basics In today’s digital landscape, the importance of server backup cannot be overstated. Businesses are increasingly relying on technology to store and manage their critical data. As such, the need to protect this information from potential loss or corruption becomes paramount. A server backup strategy is a best practice … Why Your Business Needs a Solid Server Backup Strategy: Expert Insights Read More » The post Why Your Business Needs a Solid S

Security Affairs
DECEMBER 9, 2023
Threat actors launched a cyberattack on an Irish water utility causing the interruption of the power supply for two days. Threat actors hacked a small water utility in Ireland and interrupted the water supply for two days. The victim of the attack is a private group water utility in the Erris area, the incident impacted 180 homeowners. According to the Irish media , the residents of the Binghamstown/Drum were without their water supply on Thursday and Friday.

Security Boulevard
DECEMBER 9, 2023
Many thanks to DEF CON 31 for publishing their terrific DefCon Conference 31 presenters content. Originating from the conference events at Caesars Forum, Flamingo, Harrah’s and Linq in Las Vegas, Nevada ; via the organizations YouTube channel. Permalink The post DEF CON 31 Car Hacking Village – Euntae Jang’s, Donghyon Jeong’s, Jonghyuk Song’s ‘Automotive USB Fuzzing’ appeared first on Security Boulevard.
Let's personalize your content