Burglars Using Wi-Fi Jammers to Disable Security Cameras
Schneier on Security
MARCH 13, 2024
The arms race continues, as burglars are learning how to use jammers to disable Wi-Fi security cameras.

Schneier on Security
MARCH 13, 2024
The arms race continues, as burglars are learning how to use jammers to disable Wi-Fi security cameras.

Penetration Testing
MARCH 13, 2024
Security researchers have disclosed two vulnerabilities (CVE-2024-23672 and CVE-2024-24549) in popular Apache Tomcat web server software. Organizations relying on Tomcat must prioritize updates to mitigate denial of service (DoS) attacks exploiting these flaws. What’s... The post Apache Tomcat Vulnerabilities Exposed, Prompt Updates Required appeared first on Penetration Testing.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
MARCH 13, 2024
Fortinet patched a critical vulnerability in its FortiClient Enterprise Management Server (EMS) software that can allow attackers to gain remote code execution (RCE) on vulnerable servers. [.
Penetration Testing
MARCH 13, 2024
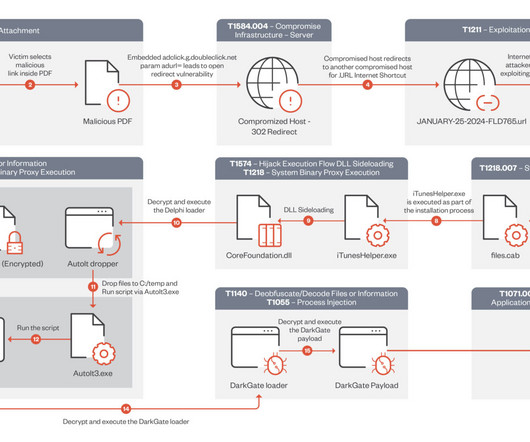
Recently, researchers at the Zero Day Initiative (ZDI) have dissected a complex DarkGate malware campaign targeting users through a zero-day flaw in Microsoft Windows SmartScreen (CVE-2024-21412). The attackers, associated with the notorious DarkGate group, are... The post New DarkGate Malware Campaign Exploits 0-day CVE-2024-21412 Flaw appeared first on Penetration Testing.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
MARCH 13, 2024
Learn about open-source password managers, the benefits, and the potential drawbacks of using these tools for managing your passwords securely.
WIRED Threat Level
MARCH 13, 2024
A global network of violent predators is hiding in plain sight, targeting children on major platforms, grooming them, and extorting them to commit horrific acts of abuse.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
MARCH 13, 2024
Microsoft’s AI chatbot and data aggregator is open for security business on April 1, with a new per-unit pricing model.

Penetration Testing
MARCH 13, 2024
The Apache Software Foundation has released urgent patches for Apache Pulsar, its versatile messaging and streaming platform. These security updates address five vulnerabilities, including potential remote code execution, unauthorized data access, and improper authentication... The post CVE-2024-27135: Apache Pulsar Remote Code Execution Vulnerability appeared first on Penetration Testing.

Security Boulevard
MARCH 13, 2024
As messaging apps like Telegram gain popularity, cybercriminals are increasingly finding they are an attractive vector for phishing attacks. The post Phishing Threats Rise as Malicious Actors Target Messaging Platforms appeared first on Security Boulevard.

Bleeping Computer
MARCH 13, 2024
The latest version of the PixPirate banking trojan for Android employs a previously unseen method to hide from the victim while remaining active on the infected device even if its dropper app has been removed. [.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Affairs
MARCH 13, 2024
Fortinet released security updates to address critical code execution vulnerabilities in FortiOS, FortiProxy, and FortiClientEMS. Fortinet this week has released security updates to fix critical code execution vulnerabilities in FortiOS, FortiProxy, and FortiClientEMS. The first vulnerability is an out-of-bounds write issue, tracked as CVE-2023-42789 (CVSS score 9.3), it can be exploited to execute unauthorized code or commands by sending specially crafted HTTP requests to vulnerable devices.

Bleeping Computer
MARCH 13, 2024
A new wave of attacks by the DarkGate malware operation exploits a now-fixed Windows Defender SmartScreen vulnerability to bypass security checks and automatically install fake software installers. [.

Security Boulevard
MARCH 13, 2024
The U.S. Department of Health and Human Services (HHS) is opening an investigation into UnitedHealth and its Change Healthcare subsidiary following a ransomware attack that for three weeks has essentially shut down payments to health care providers and hobbled pharmacies trying to fill prescriptions. Noting the “unprecedented magnitude of this cyberattack” that has rippled across.
Security Affairs
MARCH 13, 2024
Acer Philippines disclosed a data breach after employee data was leaked by a threat actor on a hacking forum. Acer Philippines confirmed that employee data was compromised in an attack targeting a third-party service provider. In our commitment to full transparency, we wish to inform you of a recent security incident involving a third-party vendor managing employee attendance data. pic.twitter.com/SXDeZ3I27B — Acer Philippines (@AcerPhils) March 12, 2024 Acer Inc. is a Taiwanese multinatio

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
MARCH 13, 2024
These seven major factors can contribute to (or hinder) the development of a positive cybersecurity culture. The post Building a Security Culture of Shared Responsibility appeared first on Security Boulevard.

Security Affairs
MARCH 13, 2024
Threat actors behind the ransomware attacks that hit Stanford University in 2023 gained access to 27,000 people. Stanford University confirmed that threat actors behind the September 2023 ransomware attack had access to 27,000 people. The prestigious US university was the victim of a ransomware attack carried out by the Akira ransomware group. The Akira ransomware gang claimed the theft of 430 GB of data from the university’s systems.

The Hacker News
MARCH 13, 2024
Google's Gemini large language model (LLM) is susceptible to security threats that could cause it to divulge system prompts, generate harmful content, and carry out indirect injection attacks. The findings come from HiddenLayer, which said the issues impact consumers using Gemini Advanced with Google Workspace as well as companies using the LLM API.
Graham Cluley
MARCH 13, 2024
Streaming company Roku has revealed that over 15,000 customers' accounts were hacked using stolen login credentials from unrelated data breaches. Read more in my article on the Hot for Security blog.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
MARCH 13, 2024
Microsoft will soon provide a single Teams Windows and macOS app for all account types that will allow users to switch between work, school, or personal profiles. [.
Security Boulevard
MARCH 13, 2024
JetBrains is continuing to criticize Rapid7’s policy for disclosing vulnerabilities its researchers uncover, saying the cybersecurity firm’s quick release of details of flaws in JetBrains’ TeamCity platform harmed some customers and runs counter to other companies’ processes. Rapid7 disclosed details of two vulnerabilities in JetBrains’ developer platform hours after the software company alerted users of.

Bleeping Computer
MARCH 13, 2024
Russian-Canadian cybercriminal Mikhail Vasiliev has been sentenced to four years in prison by an Ontario court for his involvement in the LockBit ransomware operation. [.

Penetration Testing
MARCH 13, 2024
In a detailed analysis, researchers at Cyble Research and Intelligence Labs (CRIL) have shed light on a sophisticated new threat: Xehook Stealer. This sophisticated piece of malware targets the Windows operating system and is... The post New Xehook Stealer Targets Wallets, Browsers, & More appeared first on Penetration Testing.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Bleeping Computer
MARCH 13, 2024
The U.S. Department of Health and Human Services is investigating whether protected health information was stolen in a ransomware attack that hit UnitedHealthcare Group (UHG) subsidiary Optum, which operates the Change Healthcare platform, in late February. [.

The Hacker News
MARCH 13, 2024
Fortinet has warned of a critical security flaw impacting its FortiClientEMS software that could allow attackers to achieve code execution on affected systems.

Penetration Testing
MARCH 13, 2024
Security researchers have uncovered a critical vulnerability (CVE-2024-27102) in Wings, the core component of the popular open-source Pterodactyl game server management panel. This flaw, rated a 9.9 CVSS score, could allow attackers with existing... The post CVE-2024-27102 (CVSS 9.9) Vulnerability Threatens Pterodactyl Game Servers appeared first on Penetration Testing.
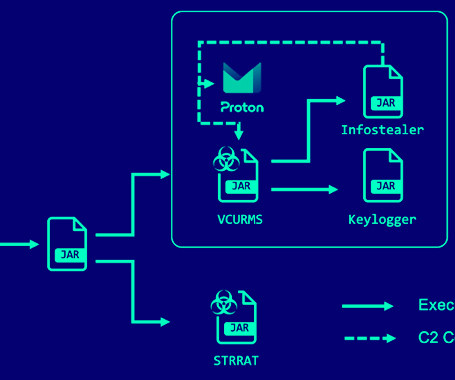
The Hacker News
MARCH 13, 2024
A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious Java-based downloader. “The attackers stored malware on public services like Amazon Web Services (AWS) and GitHub, employing a commercial protector to avoid detection of the malware,” Fortinet FortiGuard Labs researcher Yurren Wan said.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

We Live Security
MARCH 13, 2024
Here are a few tips for secure file transfers and what else to consider when sharing sensitive documents so that your data remains safe.

Bleeping Computer
MARCH 13, 2024
A new wave of attacks by the DarkGate malware operation exploits a now-fixed Windows Defender SmartScreen vulnerability to bypass security checks and automatically install fake software installers. [.

Veracode Security
MARCH 13, 2024
The release of the February 2024 White House Technical Report, Back to the Building Blocks: A Path Towards Secure Measurable Software, brings about a timely shift in prioritizing software security. Software is ubiquitous, so it’s becoming increasingly crucial to address the expanding attack surface, navigate complex regulatory environments, and mitigate the risks posed by sophisticated software supply chain attacks.

SecureList
MARCH 13, 2024
“Malvertising” is a popular way of attracting victims to malicious sites: an advertisement block is placed at the top of the search results, increasing the likelihood of users clicking the link. Sites at the top of search results also tend to be more trusted by users. A year ago, our experts discussed a malvertising campaign that spread the RedLine stealer via Google Ads.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content