Canadian Citizen Gets Phone Back from Police
Schneier on Security
JANUARY 18, 2024
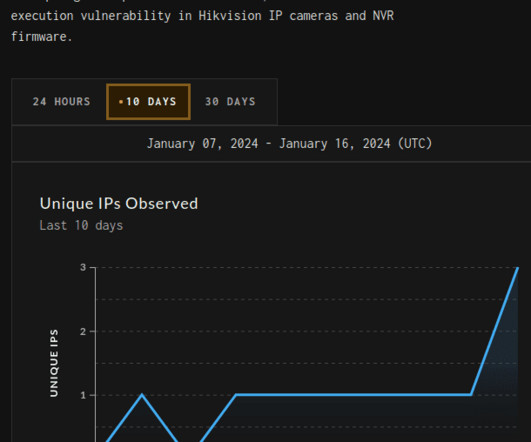
After 175 million failed password guesses, a judge rules that the Canadian police must return a suspect’s phone. [Judge] Carter said the investigation can continue without the phones, and he noted that Ottawa police have made a formal request to obtain more data from Google. “This strikes me as a potentially more fruitful avenue of investigation than using brute force to enter the phones,” he said.





































Let's personalize your content