Leaking Military Secrets on Gaming Discussion Boards
Schneier on Security
JUNE 8, 2022
People are leaking classified military information on discussion boards for the video game War Thunder to win arguments — repeatedly.

Schneier on Security
JUNE 8, 2022
People are leaking classified military information on discussion boards for the video game War Thunder to win arguments — repeatedly.

Daniel Miessler
JUNE 8, 2022
If you’ve not heard, there are these things called NFTs. I think they’re simultaneously the future of digital signaling and currently mostly hype. But whatever—that’s not what this post is about. Most NFTs rotate around a piece of collectible art in a baseball card-like format. So you look at something like the Bored Ape Yacht Club, and it’s a bunch of personalized apes with stylization.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JUNE 8, 2022
Cybercriminals are bypassing two-factor authentication using fraudulent online bot services automating phone calls, targeting multiple countries. Read more about how to protect from this threat. The post Cybercriminals use automated bot to bypass 2FA authentication at wide scale appeared first on TechRepublic.

Digital Shadows
JUNE 8, 2022
Since the beginning of the Russia-Ukraine war, hacktivism has experienced a substantial resurgence, with many hacktivist groups being created in. The post Killnet: The Hactivist Group That Started A Global Cyber War first appeared on Digital Shadows.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
JUNE 8, 2022
Security is at the heart of every business transaction carried out over the internet. Consequently, websites and web applications are becoming strict with their password requirements. The post Bitwarden vs 1Password: Password manager comparison appeared first on TechRepublic.

Security Affairs
JUNE 8, 2022
Black Basta ransomware gang implemented a new feature to encrypt VMware ESXi virtual machines (VMs) running on Linux servers. The Black Basta ransomware gang now supports encryption of VMware ESXi virtual machines (VMs) running on Linux servers. Researchers from Uptycs first reported the discovery of the new Black Basta ransomware variant that supports encryption of VMWare ESXi servers.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
The Hacker News
JUNE 8, 2022
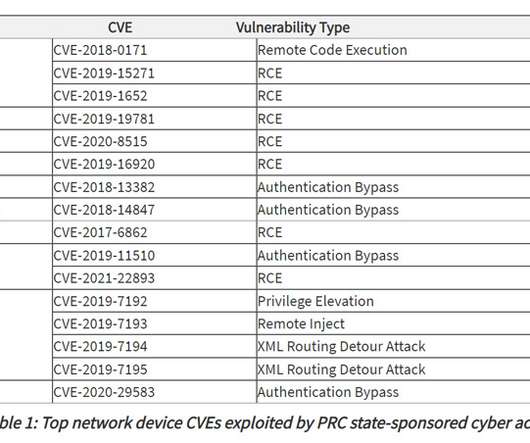
U.S. cybersecurity and intelligence agencies have warned about China-based state-sponsored cyber actors leveraging network vulnerabilities to exploit public and private sector organizations since at least 2020.

Appknox
JUNE 8, 2022
It's been a while; there has been a debate between GDPR and POPIA. Both compliances have made quite a mark since their inception.

Bleeping Computer
JUNE 8, 2022
Malware that steals your passwords, credit cards, and crypto wallets is being promoted through search results for a pirated copy of the CCleaner Pro Windows optimization program. [.].

SecureList
JUNE 8, 2022
A router is a gateway from the internet to a home or office — despite being conceived quite the opposite. Routers are forever being hacked and infected, and used to infiltrate local networks. Keeping this gate locked so that no one can stroll right through is no easy task. It is not always clear just how this locking works, especially when it comes to home routers, whose users are by no means all security pros.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

CyberSecurity Insiders
JUNE 8, 2022
Mandiant, a globally renowned Cybersecurity firm was reportedly been targeted by LockBit 2.0 Ransomware attack in May this year. And reports are in that Lockbit is interested in releasing the stolen documents, as the IT staff of Mandiant was not responding positively to its ransom demands. On the other hand, the security firm denied any kind of outside invasion on its servers and added that it lacks evidence about the claimed cyber attack by Lockbit Ransomware spreading group.

Malwarebytes
JUNE 8, 2022
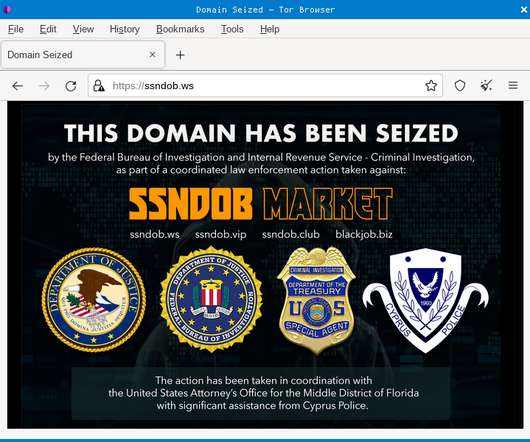
The United States Department of Justice has announced a major takedow n of a criminal marketplace that traded Personally Identifiable Information (PII). Not just any old marketplace; this was a major, years-long operation with several failsafes to prevent permanent takedown. It took quite the assortment of law enforcement worldwide to shut this one down for good.
The Hacker News
JUNE 8, 2022
An unofficial security patch has been made available for a new Windows zero-day vulnerability in the Microsoft Support Diagnostic Tool (MSDT), even as the Follina flaw continues to be exploited in the wild.

Malwarebytes
JUNE 8, 2022
A mobile app violated Canada’s privacy laws via some pretty significant overreach with its tracking of device owners. The violation will apparently not bring the app owners, Tim Hortons, any form of punishment. However, the fallout from this incident may hopefully serve as a warning to others with an app soon to launch. That’s one theory, anyway.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

CSO Magazine
JUNE 8, 2022
Looking for your next position as a CISO, preferably one with more pay, better benefits, and more on-the-job responsibilities/respect? Then you need to know what skills and qualities prospective employers are seeking now from their CISO hires to maximize your chances of getting your dream job. Here are the top six attributes recruiters sayorganizations are looking for in a CISO. 1.

Malwarebytes
JUNE 8, 2022
There’s no shortage of reasons why an SMB might use Linux to run their business: There are plenty of distros to choose from, it’s (generally) free, and perhaps above all — it’s secure. The common wisdom goes that Linux malware is rare, and for the most part this is true. Thanks to its built-in security defenses, strict user privilege model, and transparent source code, Linux enjoys far fewer malware infections than other operating systems.
Naked Security
JUNE 8, 2022
The online identity "brokerage" SSNDOB Market didn't want people to be in any doubt what it was selling.

Security Boulevard
JUNE 8, 2022
Follina (CVE-2022-30190) or the remote code execution vulnerability discovered that will abuse the Microsoft Windows Support Diagnostic Tool (MSDT.exe) in order to exploit and execute remote code was observed in Late May of 2022. The vulnerability itself was first mentioned by a security research group named "Nao Sec" via Twitter on May 27th and acknowledged by Microsoft on May 31st.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Threatpost
JUNE 8, 2022
Ransomware attackers often strike targets twice, regardless of whether the ransom was paid.

Security Boulevard
JUNE 8, 2022
The post Six things to Check before Moving to the Cloud to Avoid Pitfalls in the long run appeared first on PeoplActive. The post Six things to Check before Moving to the Cloud to Avoid Pitfalls in the long run appeared first on Security Boulevard.

Malwarebytes
JUNE 8, 2022
“A robot may not injure a human being or, through inaction, allow a human being to come to harm”. Science fiction readers, and many others, will recognize Asimov’s first law of robotics. After reading about a bot called GPT-4chan I was wondering whether we should include: “A bot may not insult a human being or, through interaction, allow a human being to be discriminated”.

CSO Magazine
JUNE 8, 2022
Microsoft will soon change the mandate to multi-factor authentication (MFA) with changes to Microsoft 365 defaults. As Microsoft points out, “When we look at hacked accounts, more than 99.9% don’t have MFA, making them vulnerable to password spray, phishing and password reuse. “Based on usage patterns, we’ll start [mandating MFA] with organizations that are a good fit for security defaults.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
JUNE 8, 2022
ReversingLabs' Jasmine Noel switched it up a bit at RSA Conference with her " Software Supply ChainSecurity Is No Game, Or Is It?" presentation, and made it an interactive experience for those watching. Her game-show for attendees made it fun, but also covered key information on the state of software supply chain security from ReversingLabs’ recent survey of 300 global IT and security professionals.

Heimadal Security
JUNE 8, 2022
An advisory recently published by multiple US federal agencies shows that Chinese state-backed cybercriminals have attacked and impacted important telecommunications organizations and network service providers in order to snatch credentials and collect sensitive data. This joint cybersecurity advisory was coauthored by the National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the […].
eSecurity Planet
JUNE 8, 2022
As part of our testing and review of Rapid7 InsightIDR , we looked at the SIEM product’s functionality and ease of use in our lab environment. InsightIDR has SIEM at its foundation and scales out to essentially be an XDR solution covering endpoints , network traffic analysis , UEBA , incident response and more. We found InsightIDR to be relatively easy to install.

Heimadal Security
JUNE 8, 2022
In January 2021, news surfaced of a ransomware strain known as Deadbolt that targets backups and is intended at serious home users, hobbyists, and small companies. Deadbolt is designed to extort money from its victims. Users who needed backups and were knowledgeable enough to make them, but who lacked the time or funds to give […]. The post Deadbolt Ransomware Uses Multi-Tiered Extortion appeared first on Heimdal Security Blog.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

We Live Security
JUNE 8, 2022
Technology is understandably viewed as a nuisance to be managed in pursuit of the health organizations’ primary mission. The post RSA – Digital healthcare meets security, but does it really want to? appeared first on WeLiveSecurity.

Security Affairs
JUNE 8, 2022
China-linked threat actors have breached telecommunications companies and network service providers to spy on the traffic and steal data. US NSA, CISA, and the FBI published a joint cybersecurity advisory to warn that China-linked threat actors have breached telecommunications companies and network service providers. The nation-state actors exploit publicly known vulnerabilities to compromise the target infrastructure. .

Identity IQ
JUNE 8, 2022
4 Ways to Avoid Payment App Scams. IdentityIQ. Peer-to-peer, or P2P, payment platforms like PayPal, Venmo, and CashApp are popular because they’re quick, convenient, and easy ways to send money to other people electronically. When used as intended, payment apps are relatively safe, but they lack some fraud protections and features that traditional payment methods like credit cards and debit cards have.

SecureBlitz
JUNE 8, 2022
In this post, I will show you 4 ways to remove Mac purgeable space. We all love to make use. Read more. The post 4 Ways To Remove Mac Purgeable Space appeared first on SecureBlitz Cybersecurity.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content