Phishing False Alarm
Schneier on Security
JANUARY 15, 2025
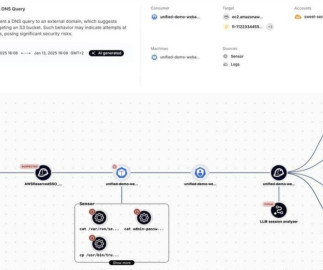
A very security-conscious company was hit with a (presumed) massive state-actor phishing attack with gift cards, and everyone rallied to combat it—until it turned out it was company management sending the gift cards.













Let's personalize your content