Critical GitHub Attack
Schneier on Security
MARCH 20, 2025
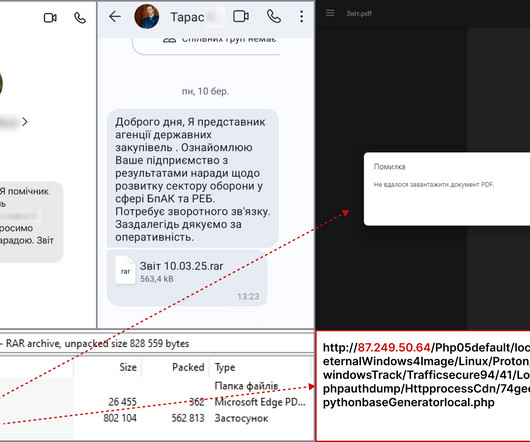
This is serious : A sophisticated cascading supply chain attack has compromised multiple GitHub Actions, exposing critical CI/CD secrets across tens of thousands of repositories. The attack, which originally targeted the widely used tj-actions/changed-files utility, is now believed to have originated from an earlier breach of the reviewdog/action-setup@v1 GitHub Action, according to a report. […] CISA confirmed the vulnerability has been patched in version 46.0.1.








































Let's personalize your content