Malicious Office 365 Apps Are the Ultimate Insiders
Krebs on Security
MAY 5, 2021
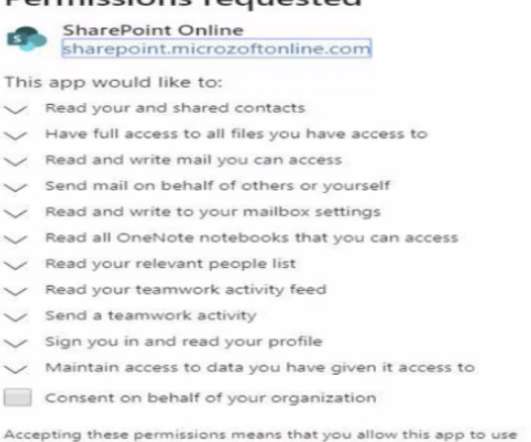
Phishers targeting Microsoft Office 365 users increasingly are turning to specialized links that take users to their organization’s own email login page. After a user logs in, the link prompts them to install a malicious but innocuously-named app that gives the attacker persistent, password-free access to any of the user’s emails and files, both of which are then plundered to launch malware and phishing scams against others.








































Let's personalize your content