Phishing attacks leveraging HTML code inside SVG files
SecureList
APRIL 21, 2025
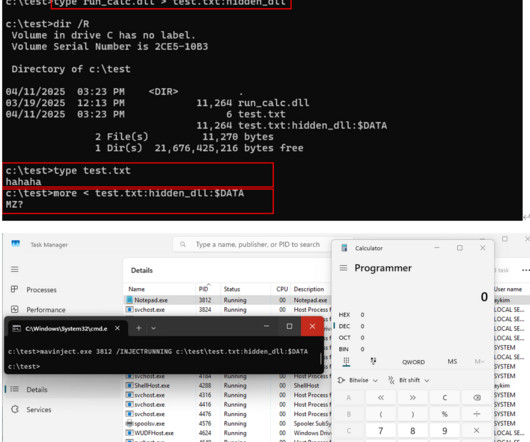
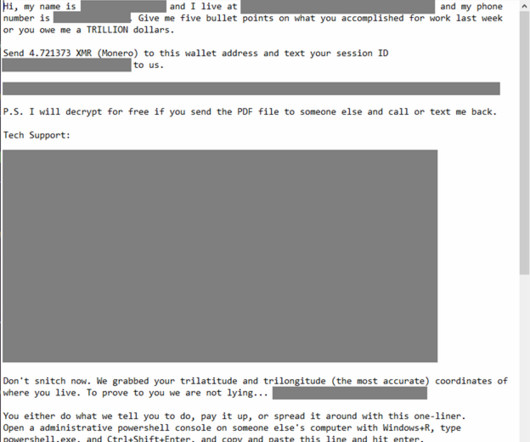
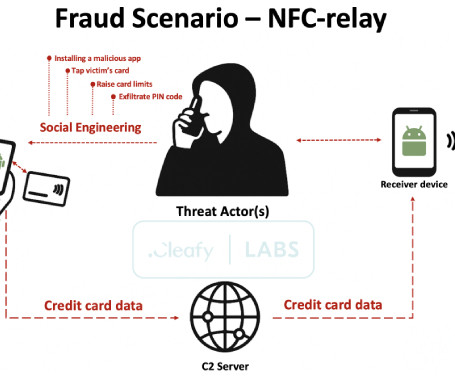
With each passing year, phishing attacks feature more and more elaborate techniques designed to trick users and evade security measures. Attackers employ deceptive URL redirection tactics, such as appending malicious website addresses to seemingly safe links, embed links in PDFs, and send HTML attachments that either host the entire phishing site or use JavaScript to launch it.





































Let's personalize your content