Camera the Size of a Grain of Salt
Schneier on Security
FEBRUARY 15, 2023
Cameras are getting smaller and smaller , changing the scale and scope of surveillance.

Schneier on Security
FEBRUARY 15, 2023
Cameras are getting smaller and smaller , changing the scale and scope of surveillance.
Tech Republic Security
FEBRUARY 15, 2023
A report reveals a new network of malefactors in the lucrative crypto fraud market using videos, channels and web apps. The post Investigators uncover crypto scammers baiting ‘phish’ hooks on YouTube appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureList
FEBRUARY 15, 2023
ChatGPT is a groundbreaking chatbot powered by the neural network-based language model text-davinci-003 and trained on a large dataset of text from the Internet. It is capable of generating human-like text in a wide range of styles and formats. ChatGPT can be fine-tuned for specific tasks, such as answering questions, summarizing text, and even solving cybersecurity-related problems, such as generating incident reports or interpreting decompiled code.

Tech Republic Security
FEBRUARY 15, 2023
The outage message that Twitter users got last week could be read as a warning for big tech firms looking to slash their IT workforce. The post What Twitter outage says about (over) zealous downsizing appeared first on TechRepublic.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Boulevard
FEBRUARY 15, 2023
Oligo Security today launched a runtime application security and observability platform that enables cybersecurity teams to detect and prioritize open source code vulnerabilities based on severity without affecting performance. Fresh from raising $28 million in funding, Oligo CEO Nadav Czerninski said the Oligo platform makes use of dynamic library-level analysis and behavior monitoring software to.

Tech Republic Security
FEBRUARY 15, 2023
Leaving your iOS device unattended can pose a security risk as more iOS users are carrying personal information on their devices. Keep it secure with these handy tips. The post How to secure your iOS device to prevent unwanted access appeared first on TechRepublic.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Trend Micro
FEBRUARY 15, 2023
We detail the intrusion set Earth Yako, attributed to the campaign Operation RestyLink or EneLink. This analysis was presented in full at the JSAC 2023 in January 2023.

CSO Magazine
FEBRUARY 15, 2023
As business processes become more complex, companies are turning to third parties to boost their ability to provide critical services from cloud storage to data management to security. It’s often more efficient and less expensive to contract out work that would otherwise require significant effort and potentially drain in-house resources to those who can do it for you.

Security Boulevard
FEBRUARY 15, 2023
It comes as no surprise that, as last year came to a close, Microsoft was tracking more than 50 unique active ransomware families and more than 100 threat actors that were using ransomware in their attacks. After all, ransomware is still a familiar, destructive and sometimes costly foe; 2022 ended with the Sandworm gang launching. The post Ransomware Closed 2022 With a Bang, Fueled by RaaS appeared first on Security Boulevard.

CSO Magazine
FEBRUARY 15, 2023
Not too long ago, guarding access to the network was the focal point of defense for security teams. Powerful firewalls ensured that attackers were blocked on the outside while on the inside things might get “squishy,” allowing users fairly free rein within. Those firewalls were the ultimate defense—no one undesirable got access. Until they did. With the advent of cloud computing, the edge of a network is no longer protected by a firewall.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Boulevard
FEBRUARY 15, 2023
As 5G networks continue to roll out, cybersecurity is top-of-mind for communication service providers (CSPs). The telecom industry was the most targeted vertical, attracting 37% of security attacks compared to 14% for the next-highest industry vertical according to CrowdStrike’s 2022 threat report. Understanding a fast-moving digital landscape comes with unique challenges, and more industries and.

CSO Magazine
FEBRUARY 15, 2023
Israel-based startup Oligo Security is exiting stealth mode with the public launch of its namesake software, offering a new wrinkle in library-based application security monitoring, observability, and remediation. Utilizing a technology called extended Berkeley Packet Filter (eBPF), it is able to provide agentless security coverage for open source code.

We Live Security
FEBRUARY 15, 2023
Don’t be their next victim – here’s a handy round-up of some the most common signs that should set your alarm bells ringing The post 10 signs that scammers have you in their sights appeared first on WeLiveSecurity
eSecurity Planet
FEBRUARY 15, 2023
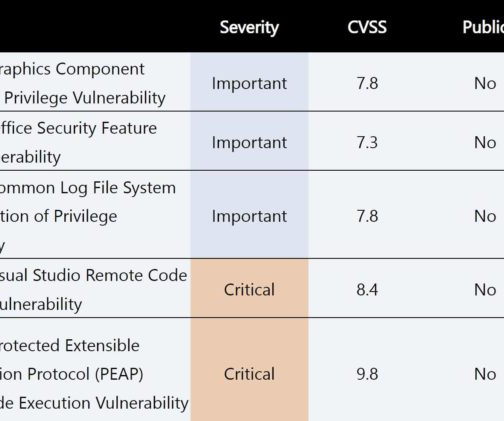
Microsoft’s February 2023 Patch Tuesday fixes 75 vulnerabilities, nine of them rated critical, and three (all rated important) that are being exploited. “This is only the second Patch Tuesday of the year, and we have already tripled the number of weaponized threats that need to be fixed in this release,” Syxsense CEO and founder Ashley Leonard told eSecurity Planet. “We also have five patches that resolve vulnerabilities with a CVSS score of more than 9 (critical), which

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

CSO Magazine
FEBRUARY 15, 2023
Descope has launched its first product, a platform designed to help developers add authentication and user management capabilities to their business-to-consumer and business-to-business applications. The software as a service is available now. Developers can access the product free of charge for up to 7,500 monthly active uses for B2C applications and up to 50 tenants for B2B apps.

Graham Cluley
FEBRUARY 15, 2023
AI-generated voices are weaponised by online trolls, how ChatGPT reflects who we are as a society, and social media is in the firing line again.

CyberSecurity Insiders
FEBRUARY 15, 2023
Are you worried about ransomware hitting your servers, putting a dent in your data intensive business? If that’s so, then Veeam Backup and Replication software is offering a data recovery warranty of $5 million from ransomware attacks. Veeam’s Premium Edition offers Modern Data Protection and Recovery capabilities against many cyber attacks, including those emerging out of file encrypting malware.

SecureWorld News
FEBRUARY 15, 2023
Vulnerability management comprises the entirety of workflows geared toward maintaining an up-to-date inventory of a company's digital assets, checking them for imperfections, and addressing the detected security loopholes. It revolves around the principle of monitoring and hardening the security condition of a corporate IT infrastructure continuously to ensure proactive defenses against different forms of exploitation.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Heimadal Security
FEBRUARY 15, 2023
Also known as operational security or procedural security, OPSEC is a security and risk management process that prevents sensitive information from falling into the hands of malicious actors. Originating in the military, OPSEC became a popular practice in the private sector as well, helping organizations to protect customer data, address cyberespionage, and information security.

Identity IQ
FEBRUARY 15, 2023
Global Marketing Leader Pam El Joins the IDIQ Board of Directors IdentityIQ -Veteran marketer brings decades of experience working with billion-dollar brands such as the NBA, Nationwide Financial and State Farm to IDIQ- Temecula, CA, Feb. 15, 2023— IDIQ , an industry leader in identity theft protection and credit monitoring, today announced the appointment of Pam El, a marketing veteran and former executive vice president and chief marketing officer at the National Basketball Association, to its

Heimadal Security
FEBRUARY 15, 2023
Researchers discovered that the Tap Busters: Bounty Hunters app had left their database open to the public for at least five months, exposing users’ private conversations. Additionally, sensitive data was hardcoded into the client side of the app, making it vulnerable to further leaks. With over one million downloads on Google Play Store and more […] The post 1 Million Downloads Later: How An Android Game Leaked Private Data appeared first on Heimdal Security Blog.

The Hacker News
FEBRUARY 15, 2023
Cybersecurity researchers have unearthed a new piece of evasive malware dubbed Beep that's designed to fly under the radar and drop additional payloads onto a compromised host. "It seemed as if the authors of this malware were trying to implement as many anti-debugging and anti-VM (anti-sandbox) techniques as they could find," Minerva Labs researcher Natalie Zargarov said.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

CyberSecurity Insiders
FEBRUARY 15, 2023
First is the news about the compromise of a SAS network as hackers disrupted Scandinavian airlines computer network and accessed information related to thousands of customers. Karin Nyman, the in-charge spokesperson of SAS, stated that his company was working on remediating the effects of the digital attack and urged customers to stay away from the mobile app for now.

Dark Reading
FEBRUARY 15, 2023
US federal watchdog agency outlines key measures for better protecting sensitive data under the federal government's control.

WIRED Threat Level
FEBRUARY 15, 2023
After 16 years, the agency has implemented the software to cryptographically verify digital passport data—and it’s already caught a dozen alleged fraudsters.

Graham Cluley
FEBRUARY 15, 2023
Towards the end of last year, malicious hackers broke into the systems of Pepsi Bottling Ventures, the largest privately-owned bottler of Pepsi-Cola beverages in the USA, and installed malware. For almost the month the malware secretly exfiltrated personally identifiable information (PII) from the company's network. Read more in my article on the Hot for Security blog.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
FEBRUARY 15, 2023
Citrix released security updates for multiple High-Severity flaws in Virtual Apps and Desktops, and Workspace apps for Windows and Linux. Citrix released security patches to fix multiple vulnerabilities in Virtual Apps and Desktops, and Workspace apps for Windows and Linux. The first issue listed in the support Knowledge Center of the company, tracked as CVE-2023-24483 , is a Privilege Escalation to NT AUTHORITYSYSTEM on the vulnerable VDA. “A vulnerability has been identified that, if exp

Heimadal Security
FEBRUARY 15, 2023
Protecting your computer from malicious attacks is an important part of keeping it safe and secure. But with the vast array of antivirus and anti-malware programs available, it can be difficult to determine which one is best for your needs. A successful malware attack has great impact on both users and organizations, causing data loss, […] The post Antivirus versus Anti Malware: Which One Should You Choose?

Security Affairs
FEBRUARY 15, 2023
Adobe Patch Tuesday addressed at least a half dozen vulnerabilities, including critical issues that expose Windows and macOS to hack. Adobe released security updates to address at least a half dozen vulnerabilities impacting Photoshop, Illustrator and After Effects for both Windows and macOS users. Adobe addressed four critical issues (CVE-2022-24094, CVE-2022-24095, CVE-2022-24096, and CVE-2022-24097) affecting the After Effects products, successful exploitation could lead to arbitrary code exe

Security Boulevard
FEBRUARY 15, 2023
Data Loss Prevention, commonly referred to as DLP, refers to policies, technologies, and controls used by organizations to prevent accidental leaks, misuse, or intentional theft of sensitive data by users, malicious insiders, or external attackers. Strategies can include forcing encryption of shared data, restricting access to sensitive data to only those employees with legitimate needs, … Continued The post What is Data Loss Prevention?

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content