GUEST ESSAY: ‘Nag attacks’ — this new phishing variant takes full advantage of notification fatigue
The Last Watchdog
NOVEMBER 29, 2022
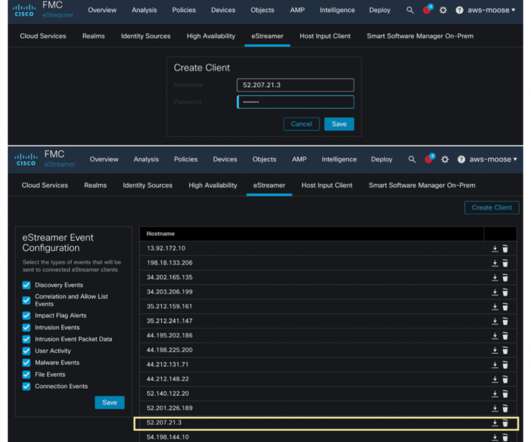
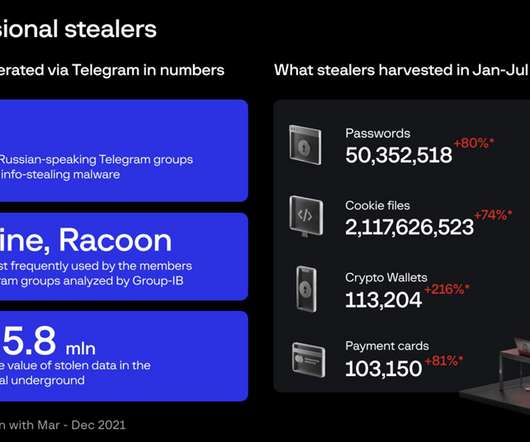
One must admire the ingenuity of cybercriminals. Related: Thwarting email attacks. A new development in phishing is the “nag attack.” The fraudster commences the social engineering by irritating the targeted victim, and then follows up with an an offer to alleviate the annoyance. The end game, of course, is to trick an intended victim into revealing sensitive information or it could be to install malicious code.



































Let's personalize your content