A threat actor is selling access to Facebook and Instagram’s Police Portal
Security Affairs
OCTOBER 21, 2023
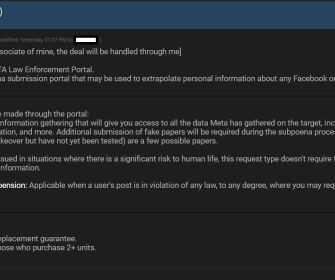
A threat actor is selling access to Facebook and Instagram’s Police Portal used by law enforcement agencies to request data relating to users under investigation. Cyber security researcher Alon Gal, co-founder & CTO of Hudson Rock, first reported that a threat actor is selling access to Facebook and Instagram’s Police Portal. The portal allows law enforcement agencies to request data relating to users (IP, phones, DMs, device info) or request the removal of posts and the ban of a



















Let's personalize your content