Crashing iPhones with a Flipper Zero
Schneier on Security
NOVEMBER 6, 2023
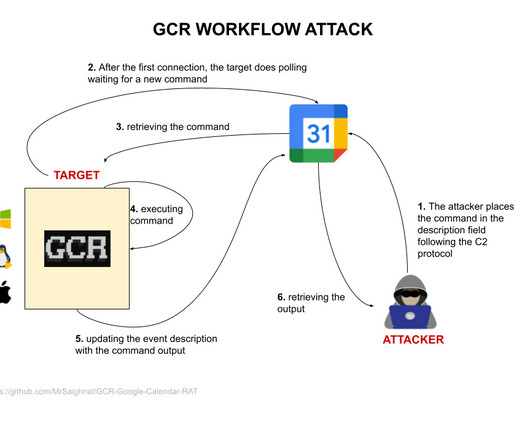
The Flipper Zero is an incredibly versatile hacking device. Now it can be used to crash iPhones in its vicinity by sending them a never-ending stream of pop-ups. These types of hacks have been possible for decades, but they require special equipment and a fair amount of expertise. The capabilities generally required expensive SDRs—short for software-defined radios—that, unlike traditional hardware-defined radios, use firmware and processors to digitally re-create radio signal tran









































Let's personalize your content