Pwned - The Collected Blog Posts of Troy Hunt (Preview)
Troy Hunt
OCTOBER 20, 2021
We choose this photo for the cover because this was when it all started. 18-year old Troy, having just discovered the web in early 1995 and chomping at the bit to do something with it. The full tale of what I first did (and how disastrous it ultimately became), is up front early in the book so I won't relay it here, but it's quite the story.


























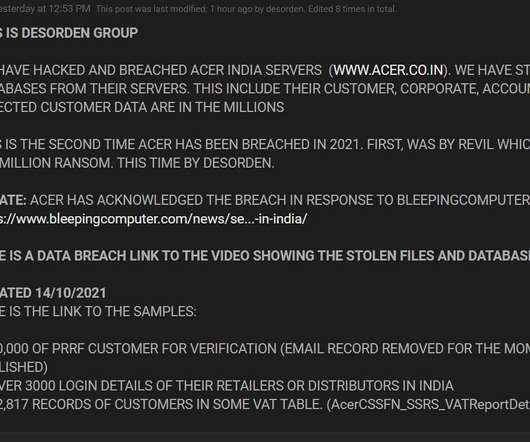













Let's personalize your content