ChatGPT Privacy Flaw
Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

The Last Watchdog
MARCH 22, 2023
APIs have been a linchpin as far as accelerating digital transformation — but they’ve also exponentially expanded the attack surface of modern business networks. Related: Why ‘attack surface management’ has become crucial The resultant benefits-vs-risks gap has not surprisingly attracted the full attention of cyber criminals who now routinely leverage API weaknesses in all phases of sophisticated, multi-stage network attacks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MARCH 22, 2023
New report says far too many firms have too many IT assets they cannot see or aren’t using, with some Windows servers lacking endpoint protection and patch management. The post Report: Too many enterprises have shadow IT – unlocked doors with no cameras appeared first on TechRepublic.
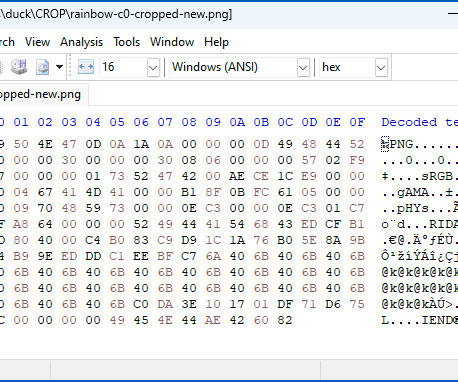
Naked Security
MARCH 22, 2023
Turns out that the Windows 11 Snipping Tool has the same "aCropalypse" data leakage bug as Pixel phones. Here's how to work around the problem.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

CyberSecurity Insiders
MARCH 22, 2023
Cybercriminals are smarter, faster, and more relentless in their attacks than in times past. Data breaches are a serious threat to organizations, but vulnerability management automation can help reduce the number of incidents businesses face each year. Managing vulnerabilities is difficult in an increasingly connected cyber environment. Companies have their own networks, networks connected to their supply chains, vendor access, remote workers, and other entry points, all creating security gaps.

Graham Cluley
MARCH 22, 2023
Graham Cluley Security News is sponsored this week by the folks at Sysdig. Thanks to the great team there for their support! What is one of the leading causes of breaches in the cloud? OMG, it’s still phishing! It’s no wonder CISOs push zero trust as a top priority. Identities are a top cloud target.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Heimadal Security
MARCH 22, 2023
A new campaign is deploying variants of the ShellBot malware, specifically targeting poorly maintained Linux SSH servers. It seems the threat actors use scanner malware to find systems that have SSH port 22 open and proceed to install ShellBot on the servers that have weak credentials. ShellBot, also known as PerlBot, is a DDoS Bot […] The post ShellBot DDoS Malware Targets Poorly Managed Linux Servers appeared first on Heimdal Security Blog.

Bleeping Computer
MARCH 22, 2023
On the first day of Pwn2Own Vancouver 2023, security researchers successfully demoed Tesla Model 3, Windows 11, and macOS zero-day exploits and exploit chains to win $375,000 and a Tesla Model 3. [.

Security Through Education
MARCH 22, 2023
What does a government scam, an IT support scam and a romance scam have in common? They all use psychology and social engineering skills to convince their victims to take an action that is detrimental to them. It’s easy to think “I know better” or “that will never happen to me.” The truth is, being human is enough for anyone to fall victim to a scammer’s tactics.

Trend Micro
MARCH 22, 2023
After months of investigation, we found that several undisclosed malware and interesting tools used for exfiltration purposes were being used by Earth Preta. We also observed that the threat actors were actively changing their tools, tactics, and procedures (TTPs) to bypass security solutions. In this blog entry, we will introduce and analyze the other tools and malware used by the threat actor.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Bleeping Computer
MARCH 22, 2023
A trojanized version of the legitimate ChatGPT extension for Chrome is gaining popularity on the Chrome Web Store, accumulating over 9,000 downloads while stealing Facebook accounts. [.

CSO Magazine
MARCH 22, 2023
The average enterprise storage and backup device has 14 vulnerabilities, three of which are high or critical risk that could present a significant compromise if exploited. That’s according to Continuity’s State of Storage and Backup Security Report 2023 , which revealed a significant gap in the state of enterprise storage and backup security compared to other layers of IT and network security.

Bleeping Computer
MARCH 22, 2023
A new credit card stealing hacking campaign is doing things differently than we have seen in the past by hiding their malicious code inside the 'Authorize.net' payment gateway module for WooCommcerce, allowing the breach to evade detection by security scans. [.

Graham Cluley
MARCH 22, 2023
It could be a case of aCropalypse now for Google Pixel users, there’s a warning for house buyers, and just why is TikTok being singled out for privacy concerns? All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Thom Langford.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

CSO Magazine
MARCH 22, 2023
The furor surrounding ChatGPT remains at a fever pitch as the ins and outs of the AI chatbot’s potential continue to make headlines. One issue that has caught the attention of many in the security field is whether the technology’s ingestion of sensitive business data puts organizations at risk. There is some fear that if one inputs sensitive information — quarterly reports, materials for an internal presentation, sales numbers, or the like — and asks ChatGPT to write text around it, that anyone

Dark Reading
MARCH 22, 2023
Attackers claiming to be part of the Chinese navy are making calls to commercial Qantas pilots midair, while GPS, comms systems, and altimeter instruments are all experiencing denial of service.

eSecurity Planet
MARCH 22, 2023
Networks connect devices to each other so that users can access assets such as applications, data, or even other networks such as the internet. Network security protects and monitors the links and the communications within the network using a combination of hardware, software, and enforced policies. Networks and network security comes in a wide range of complexity to fit the wide range of needs.

Dark Reading
MARCH 22, 2023
A new Tech Insight report examines how the enterprise attack surface is expanding and how organizations must deal with vulnerabilities in emerging technologies.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

CSO Magazine
MARCH 22, 2023
New security and observability features will be added to Splunk Mission Control and its Observability Cloud to identify threats and incidents more efficiently, the company said.

Dark Reading
MARCH 22, 2023
The advisory comes the same week as a warning from the EU's ENISA about potential for ransomware attacks on OT systems in the transportation sector.

Heimadal Security
MARCH 22, 2023
Hitachi Energy confirmed that it was the victim of a data breach, part of the GoAnywhere attacks. The Clop ransomware gang exploited a Fortra GoAnywhere MFT (Managed File Transfer) zero-day vulnerability to gain access. The Japanese engineering and technology giant provides energy solutions and power systems. Hitachi Energy has a $10 billion yearly income.

Bleeping Computer
MARCH 22, 2023
A joint cybersecurity advisory from the German Federal Office for the Protection of the Constitution (BfV) and the National Intelligence Service of the Republic of Korea (NIS) warn about Kimsuky's use of Chrome extensions to steal target's Gmail emails. [.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Malwarebytes
MARCH 22, 2023
Tax season is upon us and, as with every year, we're seeing tax scammers rearing their heads. Below, we have an example of a tax scam currently in circulation along with some suggestions for avoiding these kinds of attacks. An IRS W-9 tax form scam A Form W-9 is a form you fill in to confirm certain personal details with the IRS. Name, address, and Tax Identification Number are all things you can expect to fill in on one of these forms.
Security Affairs
MARCH 22, 2023
Cisco Talos researchers published PoC exploits for vulnerabilities in Netgear Orbi 750 series router and extender satellites. Netgear Orbi is a line of mesh Wi-Fi systems designed to provide high-speed, reliable Wi-Fi coverage throughout a home or business. The Orbi system consists of a main router and one or more satellite units that work together to create a seamless Wi-Fi network that can cover a large area with consistent, high-speed Wi-Fi.

SecureWorld News
MARCH 22, 2023
Ferrari has disclosed a data breach following a ransom demand received from attackers that gained access to some of the company's IT systems. While the luxury sports car maker said the attackers gained access to its network and then demanded a ransom not to leak data stolen from its systems, Ferrari is yet to disclose if this was a ransomware attack or just an extortion attempt.
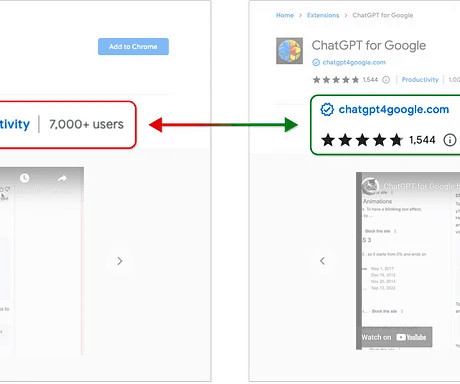
Security Affairs
MARCH 22, 2023
A tainted version of the legitimate ChatGPT extension for Chrome, designed to steal Facebook accounts, has thousands of downloads. Guardio ’s security team uncovered a new variant of a malicious Chat-GPT Chrome Extension that was already downloaded by thousands a day. The version employed in a recent campaign is based on a legitimate open-source project , threat actors added malicious code to steal Facebook accounts.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Graham Cluley
MARCH 22, 2023
Have you ever shared a photograph where you've redacted some sensitive information? Perhaps you've cropped out part of the image you didn't want others to see? Well, users of Google's Pixel Android smartphone might be alarmed to learn that pictures they've shared in the past may have been less discreet than they imagined. Read more in my article on the Hot for Security blog.

Security Affairs
MARCH 22, 2023
The European Union Agency for Cybersecurity (ENISA) published its first cyber threat landscape report for the transport sector. A new report published by the European Union Agency for Cybersecurity (ENISA) analyzes threats and incidents in the transport sector. The report covers incidents in aviation, maritime, railway, and road transport industries between January 2021 and October 2022.

GlobalSign
MARCH 22, 2023
In this blog, we take a look at 3 common challenges that face IoT security.
Security Affairs
MARCH 22, 2023
US health services company Independent Living Systems (ILS) discloses a data breach that impacted more than 4 million individuals. US health services company Independent Living Systems (ILS) disclosed a data breach that exposed personal and medical information for more than 4 million individuals. Independent Living Systems, offers a comprehensive range of turnkey payer services including clinical and third-party administrative services to managed care organizations and providers.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content