ChatGPT Privacy Flaw
Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

The Last Watchdog
MARCH 22, 2023
APIs have been a linchpin as far as accelerating digital transformation — but they’ve also exponentially expanded the attack surface of modern business networks. Related: Why ‘attack surface management’ has become crucial The resultant benefits-vs-risks gap has not surprisingly attracted the full attention of cyber criminals who now routinely leverage API weaknesses in all phases of sophisticated, multi-stage network attacks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MARCH 22, 2023
New report says far too many firms have too many IT assets they cannot see or aren’t using, with some Windows servers lacking endpoint protection and patch management. The post Report: Too many enterprises have shadow IT – unlocked doors with no cameras appeared first on TechRepublic.

CyberSecurity Insiders
MARCH 22, 2023
Cybercriminals are smarter, faster, and more relentless in their attacks than in times past. Data breaches are a serious threat to organizations, but vulnerability management automation can help reduce the number of incidents businesses face each year. Managing vulnerabilities is difficult in an increasingly connected cyber environment. Companies have their own networks, networks connected to their supply chains, vendor access, remote workers, and other entry points, all creating security gaps.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
MARCH 22, 2023
On the first day of Pwn2Own Vancouver 2023, security researchers successfully demoed Tesla Model 3, Windows 11, and macOS zero-day exploits and exploit chains to win $375,000 and a Tesla Model 3. [.

CyberSecurity Insiders
MARCH 22, 2023
Is your organization doing enough to protect its environment from hackers? In 2021, U.S. companies lost nearly $7 billion to phishing scams, malware, malvertising, and other cybercrimes. Experts estimate that by 2025, such schemes will cost businesses worldwide more than $10.5 trillion annually. Given those figures, it’s clear that companies can’t afford to ignore the threat hackers pose to their bottom line.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
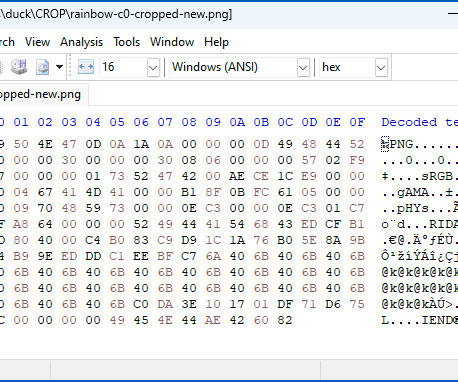
Naked Security
MARCH 22, 2023
Turns out that the Windows 11 Snipping Tool has the same "aCropalypse" data leakage bug as Pixel phones. Here's how to work around the problem.

Security Through Education
MARCH 22, 2023
What does a government scam, an IT support scam and a romance scam have in common? They all use psychology and social engineering skills to convince their victims to take an action that is detrimental to them. It’s easy to think “I know better” or “that will never happen to me.” The truth is, being human is enough for anyone to fall victim to a scammer’s tactics.

Bleeping Computer
MARCH 22, 2023
A trojanized version of the legitimate ChatGPT extension for Chrome is gaining popularity on the Chrome Web Store, accumulating over 9,000 downloads while stealing Facebook accounts. [.

CSO Magazine
MARCH 22, 2023
The average enterprise storage and backup device has 14 vulnerabilities, three of which are high or critical risk that could present a significant compromise if exploited. That’s according to Continuity’s State of Storage and Backup Security Report 2023 , which revealed a significant gap in the state of enterprise storage and backup security compared to other layers of IT and network security.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Heimadal Security
MARCH 22, 2023
A new campaign is deploying variants of the ShellBot malware, specifically targeting poorly maintained Linux SSH servers. It seems the threat actors use scanner malware to find systems that have SSH port 22 open and proceed to install ShellBot on the servers that have weak credentials. ShellBot, also known as PerlBot, is a DDoS Bot […] The post ShellBot DDoS Malware Targets Poorly Managed Linux Servers appeared first on Heimdal Security Blog.

CSO Magazine
MARCH 22, 2023
The furor surrounding ChatGPT remains at a fever pitch as the ins and outs of the AI chatbot’s potential continue to make headlines. One issue that has caught the attention of many in the security field is whether the technology’s ingestion of sensitive business data puts organizations at risk. There is some fear that if one inputs sensitive information — quarterly reports, materials for an internal presentation, sales numbers, or the like — and asks ChatGPT to write text around it, that anyone

Dark Reading
MARCH 22, 2023
Attackers claiming to be part of the Chinese navy are making calls to commercial Qantas pilots midair, while GPS, comms systems, and altimeter instruments are all experiencing denial of service.

CSO Magazine
MARCH 22, 2023
New security and observability features will be added to Splunk Mission Control and its Observability Cloud to identify threats and incidents more efficiently, the company said.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Bleeping Computer
MARCH 22, 2023
A joint cybersecurity advisory from the German Federal Office for the Protection of the Constitution (BfV) and the National Intelligence Service of the Republic of Korea (NIS) warn about Kimsuky's use of Chrome extensions to steal target's Gmail emails. [.

Dark Reading
MARCH 22, 2023
A new Tech Insight report examines how the enterprise attack surface is expanding and how organizations must deal with vulnerabilities in emerging technologies.

Malwarebytes
MARCH 22, 2023
Tax season is upon us and, as with every year, we're seeing tax scammers rearing their heads. Below, we have an example of a tax scam currently in circulation along with some suggestions for avoiding these kinds of attacks. An IRS W-9 tax form scam A Form W-9 is a form you fill in to confirm certain personal details with the IRS. Name, address, and Tax Identification Number are all things you can expect to fill in on one of these forms.

Dark Reading
MARCH 22, 2023
The advisory comes the same week as a warning from the EU's ENISA about potential for ransomware attacks on OT systems in the transportation sector.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
MARCH 22, 2023
Poor password practices continue to put businesses at risk, with nearly 90% of passwords used in successful attacks consisting of 12 characters or less, indicating additional security measures are required to protect access to sensitive data. These were among the results of a Specops Software report analyzing more than 800 million breached passwords.
The Hacker News
MARCH 22, 2023
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia. The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "network-based forms of detection.

Security Boulevard
MARCH 22, 2023
Earlier this year, the PCI Security Standards Council revealed version 4.0 of their payment card industry data security standard (PCI-DSS). While organizations won’t need to be fully compliant with 4.0 until March 2025, this update is their most transformative to date and will require most businesses to assess (and likely upgrade) complex security processes and.

Trend Micro
MARCH 22, 2023
After months of investigation, we found that several undisclosed malware and interesting tools used for exfiltration purposes were being used by Earth Preta. We also observed that the threat actors were actively changing their tools, tactics, and procedures (TTPs) to bypass security solutions. In this blog entry, we will introduce and analyze the other tools and malware used by the threat actor.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.
The Hacker News
MARCH 22, 2023
The North Korean advanced persistent threat (APT) actor dubbed ScarCruft is using weaponized Microsoft Compiled HTML Help (CHM) files to download additional malware. According to multiple reports from AhnLab Security Emergency response Center (ASEC), SEKOIA.IO, and Zscaler, the development is illustrative of the group's continuous efforts to refine and retool its tactics to sidestep detection.

Bleeping Computer
MARCH 22, 2023
Microsoft has released a new Windows 11 preview build that adds a new dedicated USB4 settings page and support for displaying seconds in the system tray clock. [.
Security Affairs
MARCH 22, 2023
Cisco Talos researchers published PoC exploits for vulnerabilities in Netgear Orbi 750 series router and extender satellites. Netgear Orbi is a line of mesh Wi-Fi systems designed to provide high-speed, reliable Wi-Fi coverage throughout a home or business. The Orbi system consists of a main router and one or more satellite units that work together to create a seamless Wi-Fi network that can cover a large area with consistent, high-speed Wi-Fi.

SecureBlitz
MARCH 22, 2023
Is there safe streaming for everyone? Read on to find out. The entertainment world has undergone a major shift in recent years, with streaming platforms such as Netflix, Amazon Prime, and Disney+ becoming more popular. Gone are the days of having to schedule your TV watching around set times and channels, as these platforms allow […] The post Safe Streaming For Everyone appeared first on SecureBlitz Cybersecurity.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

CyberSecurity Insiders
MARCH 22, 2023
So far, the geologists across the globe had a brief opportunity to detect life on Mars. But a new study says that the technology of Artificial Intelligence (AI) can help in detecting the hidden patterns withing a geographical data and assure whether there is any existence of life on the second smallest planet in the solar system. Using AI and ML tools, an international team of 50 scientists launched a mission to detect extra-terrestrial life on the 4th planet from the Sun.

Bleeping Computer
MARCH 22, 2023
Proof-of-concept exploits for vulnerabilities in Netgear's Orbi 750 series router and extender satellites have been released, with one flaw a critical severity remote command execution bug. [.
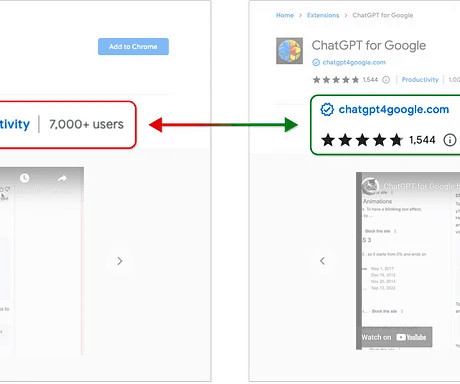
Security Affairs
MARCH 22, 2023
A tainted version of the legitimate ChatGPT extension for Chrome, designed to steal Facebook accounts, has thousands of downloads. Guardio ’s security team uncovered a new variant of a malicious Chat-GPT Chrome Extension that was already downloaded by thousands a day. The version employed in a recent campaign is based on a legitimate open-source project , threat actors added malicious code to steal Facebook accounts.

Graham Cluley
MARCH 22, 2023
Have you ever shared a photograph where you've redacted some sensitive information? Perhaps you've cropped out part of the image you didn't want others to see? Well, users of Google's Pixel Android smartphone might be alarmed to learn that pictures they've shared in the past may have been less discreet than they imagined. Read more in my article on the Hot for Security blog.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content