Have You Factored Cybersecurity Infrastructure into Your Global Growth?
GlobalSign
AUGUST 14, 2023
As companies extend their operations globally, they must prioritise cybersecurity measures to support sustainable long-term growth. Read more.

GlobalSign
AUGUST 14, 2023
As companies extend their operations globally, they must prioritise cybersecurity measures to support sustainable long-term growth. Read more.

The Last Watchdog
AUGUST 13, 2023
LAS VEGAS – Just when we appeared to be on the verge of materially shrinking the attack surface, along comes an unpredictable, potentially explosive wild card: generative AI. Related: Can ‘CNAPP’ do it all? Unsurprisingly, generative AI was in the spotlight at Black Hat USA 2023 , which returned to its full pre-Covid grandeur here last week.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
AUGUST 15, 2023
This is why we need regulation: Zoom updated its Terms of Service in March, spelling out that the company reserves the right to train AI on user data with no mention of a way to opt out. On Monday, the company said in a blog post that there’s no need to worry about that. Zoom execs swear the company won’t actually train its AI on your video calls without permission, even though the Terms of Service still say it can.

Troy Hunt
AUGUST 14, 2023
I've been teaching my 13-year old son Ari how to code since I first got him started on Scratch many years ago, and gradually progressed through to the current day where he's getting into Python in Visual Studio Code. As I was writing the new domain search API for Have I Been Pwned (HIBP) over the course of this year, I was trying to explain to him how powerful APIs are: Think of HIBP as one website that does pretty much one thing; you load it in your browser and search through data bre

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.

Krebs on Security
AUGUST 17, 2023
You’ve probably never heard of “ 16Shop ,” but there’s a good chance someone using it has tried to phish you. A 16Shop phishing page spoofing Apple and targeting Japanese users. Image: Akamai.com. The international police organization INTERPOL said last week it had shuttered the notorious 16Shop, a popular phishing-as-a-service platform launched in 2017 that made it simple for even complete novices to conduct complex and convincing phishing scams.

Tech Republic Security
AUGUST 14, 2023
With security schema, Splunk and collaborators aim to transform alert telemetry from cacophony to chorus with one taxonomy across vendors and tools.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
AUGUST 17, 2023
A previously undetected attack method called NoFilter has been found to abuse the Windows Filtering Platform (WFP) to achieve privilege escalation in the Windows operating system.
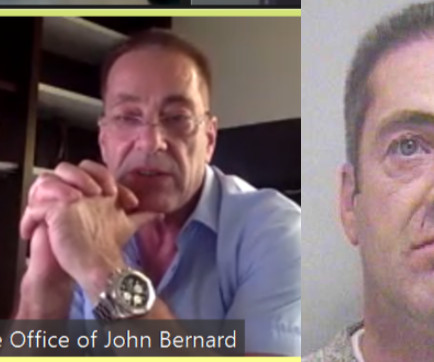
Krebs on Security
AUGUST 14, 2023
John Clifton Davies , a convicted fraudster estimated to have bilked dozens of technology startups out of more than $30 million through phony investment schemes, has a brand new pair of scam companies that are busy dashing startup dreams: A fake investment firm called Equity-Invest[.]ch , and Diligere[.]co.uk , a scam due diligence company that Equity-Invest insists all investment partners use.

Tech Republic Security
AUGUST 17, 2023
Learn how to retrieve and generate Google 2FA backup codes with this easy-to-follow, step-by-step tutorial.

Schneier on Security
AUGUST 14, 2023
The NSA discovered the intrusion in 2020—we don’t know how—and alerted the Japanese. The Washington Post has the story : The hackers had deep, persistent access and appeared to be after anything they could get their hands on—plans, capabilities, assessments of military shortcomings, according to three former senior U.S. officials, who were among a dozen current and former U.S. and Japanese officials interviewed, who spoke on the condition of anonymity because of the matte

Speaker: Speakers:
In today's digital age, having an untrained workforce can be a significant risk to your business. Cyber threats are evolving; without proper training, your employees could be the weakest link in your defense. This webinar empowers leaders like you with the tools and strategies needed to transform your employees into a robust frontline defense against cyber attacks.

The Hacker News
AUGUST 18, 2023
Threat actors are using Android Package (APK) files with unknown or unsupported compression methods to elude malware analysis. That's according to findings from Zimperium, which found 3,300 artifacts leveraging such compression algorithms in the wild. 71 of the identified samples can be loaded on the operating system without any problems.

Bleeping Computer
AUGUST 18, 2023
A high-severity vulnerability has been fixed in WinRAR, the popular file archiver utility for Windows used by millions, that can execute commands on a computer simply by opening an archive. [.

Tech Republic Security
AUGUST 17, 2023
Code development, content creation and analytics are the top generative AI use cases. However, many enterprise users don't trust gen AI to be private.

Schneier on Security
AUGUST 18, 2023
Interesting research: “ An Empirical Study & Evaluation of Modern CAPTCHAs “: Abstract: For nearly two decades, CAPTCHAS have been widely used as a means of protection against bots. Throughout the years, as their use grew, techniques to defeat or bypass CAPTCHAS have continued to improve. Meanwhile, CAPTCHAS have also evolved in terms of sophistication and diversity, becoming increasingly difficult to solve for both bots (machines) and humans.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

The Hacker News
AUGUST 18, 2023
Microsoft on Thursday disclosed that it found a new version of the BlackCat ransomware (aka ALPHV and Noberus) that embeds tools like Impacket and RemCom to facilitate lateral movement and remote code execution.

Bleeping Computer
AUGUST 17, 2023
A very useful and previously unknown Windows tip was revealed this week, where you can halt process jumping in Task Manager by holding down the Ctrl key on your keyboard, allowing easier access to a listed process. [.

Tech Republic Security
AUGUST 16, 2023
Generative AI landed on Gartner's coveted Hype Cycle for Emerging Technologies for 2023. Read about AI's transformational impact on business and society.

Schneier on Security
AUGUST 17, 2023
Researchers are trying to use AI to detect “social norms violations.” Feels a little sketchy right now, but this is the sort of thing that AIs will get better at. (Like all of these systems, anything but a very low false positive rate makes the detection useless in practice.) News article.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

The Hacker News
AUGUST 17, 2023
Google has announced plans to add a new feature in the upcoming version of its Chrome web browser to alert users when an extension they have installed has been removed from the Chrome Web Store. The feature, set for release alongside Chrome 117, allows users to be notified when an add-on has been unpublished by a developer, taken down for violating Chrome Web Store policy, or marked as malware.

Security Boulevard
AUGUST 17, 2023
The SEC adopted new rules surrounding cybersecurity risk management, strategy, governance, and incident disclosure. As a CISO, this no doubt impacts how your company discloses material cybersecurity incidents through a Form 8-K item and annually cybersecurity risk management and governance through the company’sForm 10-K. The final rule requires the 8-K to be filed within four […] The post New SEC Cybersecurity Rules and What It Means for Board Oversight appeared first on BlackCloak | Protec

Tech Republic Security
AUGUST 14, 2023
Unmanned aircraft systems, more commonly known as drones, have quite literally taken off by performing many new and inventive commercial applications. Delivering packages, recording terrain, reporting news, documenting wildlife and even providing internet access are just a few of the functions drones can offer. The list is sure to grow longer and more diverse as.

Graham Cluley
AUGUST 17, 2023
Security researchers have identified that a widespread LinkedIn hacking campaign has seen many users locked out of their accounts worldwide. Read more in my article on the Tripwire State of Security blog.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

The Hacker News
AUGUST 18, 2023
While IT security managers in companies and public administrations rely on the concept of Zero Trust, APTS (Advanced Persistent Threats) are putting its practical effectiveness to the test. Analysts, on the other hand, understand that Zero Trust can only be achieved with comprehensive insight into one's own network.

Security Boulevard
AUGUST 18, 2023
IBM extends its alliance with Cloudflare to combat malicious bot attacks growing in volume and sophistication. The post IBM Extends Cloudflare Alliance to Combat Bots Using Machine Learning appeared first on Security Boulevard.

Tech Republic Security
AUGUST 17, 2023
Learn seven different ways to boot a Windows 10 PC in Safe Mode to help troubleshoot issues using this comprehensive guide.

Digital Guardian
AUGUST 18, 2023
Hacks, social engineering, and phishing dominated this week’s headlines, but cloud security is at the forefront of government officials’ minds. Catch up on all the latest in this week’s Friday Five!

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

The Hacker News
AUGUST 15, 2023
Four security vulnerabilities in the ScrutisWeb ATM fleet monitoring software made by Iagona could be exploited to remotely break into ATMs, upload arbitrary files, and even reboot the terminals. The shortcomings were discovered by the Synack Red Team (SRT) following a client engagement. The issues have been addressed in ScrutisWeb version 2.1.38.

Security Boulevard
AUGUST 15, 2023
New capabilities fix security issues with MFA push notifications Zero Trust security models call for the use of multi-factor authentication (MFA) to ensure that only authorized users may access protected IT resources. Many organizations are adopting MFA to add a layer of security for remote workers. Customer-facing organizations are also implementing MFA to mitigate identity-based attacks, such as phishing, and to help quash the rise in account takeover fraud.

Tech Republic Security
AUGUST 14, 2023
This attack sent approximately 120,000 phishing emails to organizations worldwide with the goal to steal Microsoft 365 credentials.

Malwarebytes
AUGUST 14, 2023
"Freedom" is a big word, and for many parents today, it's a word that includes location tracking. Across America, parents are snapping up Apple AirTags, the inexpensive location tracking devices that can help owners find lost luggage, misplaced keys, and—increasingly so—roving toddlers setting out on mini-adventures. The parental fear right now, according to The Washington Post technology reporter Heather Kelly, is that "anybody who can walk, therefore can walk away.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Let's personalize your content