Should Technology Product Training Be Free?
Lohrman on Security
MARCH 28, 2021

We Live Security
MARCH 31, 2021
From losing cherished memories to missing deadlines, the impact of not having backups when a data disaster strikes can hardly be overstated. The post Are you prepared to prevent data loss? appeared first on WeLiveSecurity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Graham Cluley
MARCH 28, 2021
Insurance firm CNA Hardy says that it has suffered a “sophisticated cybersecurity attack” that has impacted its operations, including its email system. According to a statement posted on the firm’s website, CNA determined it had fallen foul of hackers on March 21: “Out of an abundance of caution, we have disconnected our systems from our … Continue reading "Cyber insurance giant CNA hit by ransomware attack".
Krebs on Security
MARCH 28, 2021
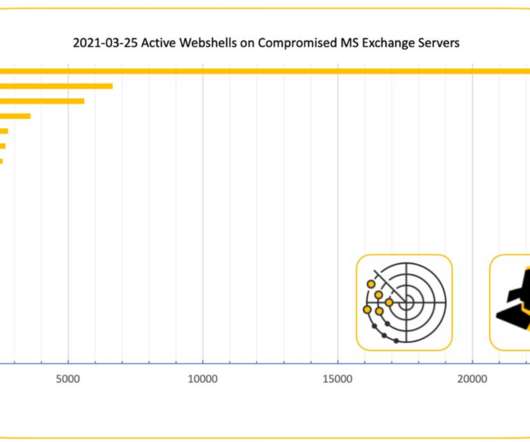
New data suggests someone has compromised more than 21,000 Microsoft Exchange Server email systems worldwide and infected them with malware that invokes both KrebsOnSecurity and Yours Truly by name. Let’s just get this out of the way right now: It wasn’t me. The Shadowserver Foundation , a nonprofit that helps network owners identify and fix security threats , says it has found 21,248 different Exchange servers which appear to be compromised by a backdoor and communicating with brian

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Schneier on Security
MARCH 30, 2021
Researchers have discovered a new Android app called “System Update” that is a sophisticated Remote-Access Trojan (RAT). From a news article : The broad range of data that this sneaky little bastard is capable of stealing is pretty horrifying. It includes: instant messenger messages and database files; call logs and phone contacts; Whatsapp messages and databases; pictures and videos; all of your text messages; and information on pretty much everything else that is on your phone (it

Tech Republic Security
MARCH 30, 2021
One way to get C-level managers and cybersecurity department heads on the same page is to employ cyber risk quantification, as it speaks to costs versus risks.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Malwarebytes
APRIL 1, 2021
A newly discovered piece of Android malware shares the same capabilities found within many modern stalkerware-type apps—it can swipe images and video, rifle through online searches, record phone calls and video, and peer into GPS location data—but the infrastructure behind the malware obscures its developer’s primary motivations. First spotted by the research team at Zimperium zLabs , the newly found malware is already detected by Malwarebytes for Android.

Schneier on Security
APRIL 1, 2021
A mafia fugitive hiding out in the Dominican Republic was arrested when investigators found his YouTube cooking channel and identified him by his distinctive arm tattoos.

Tech Republic Security
MARCH 30, 2021
KODA advising CTO John Suit discusses the skills and languages that are important for developers who want to build software and systems for modern robots.

Bleeping Computer
MARCH 29, 2021
In the latest software supply chain attack, the official PHP Git repository was hacked and tampered with. Yesterday, two malicious commits were pushed to the php-src Git repository maintained by the PHP team on their git.php.net server. The threat actors had signed off on these commits as if they were made by known PHP developers. [.].

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Malwarebytes
MARCH 29, 2021
Suppose that, out of the blue, a Steam user tells you they’ve accidentally reported you for something you didn’t do, like making an illegal purchase, and that your Steam account is going to be suspended. They ask you to message a Steam admin, whose profile they kindly provide, to help you sort out this dilemma. What do you do? There are some scams on Steam which have stood the test of time.
Graham Cluley
MARCH 31, 2021
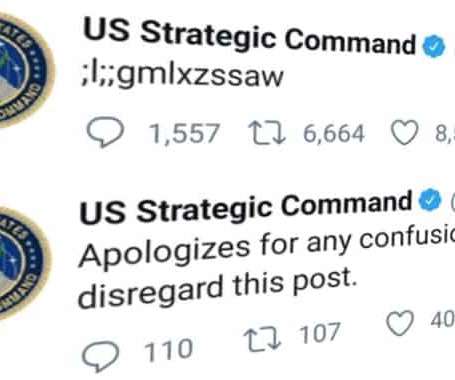
When an unintelligible tweet was made by the US Strategic Command's Twitter account, it's understandable that some folks might imagine a password was accidentally published to the world, or that perhaps the account had been compromised, or. gulp! that it might be a US nuclear launch code.

Tech Republic Security
MARCH 29, 2021
New Linux admins need to know how to give and take sudo privileges from users. Jack Wallen shows you how on both Ubuntu- and Red Hat-based Linux distributions.
Bleeping Computer
MARCH 28, 2021
Popular npm component netmask has a critical networking vulnerability, CVE-2021-28918. netmask is frequently used by hundreds of thousands of applications to parse IPv4 addresses and CIDR blocks or compare them. The component gets over 3 million weekly downloads, and as of today, has scored over 238 million total downloads. [.].

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Hot for Security
MARCH 30, 2021
Australia’s Channel 9 network disrupted by cybercriminals Staff told to work from home as station attempts to recover from attack. Live broadcasts from Australia’s Channel 9 TV network were disrupted this weekend following what is believed to have been a cyber attack. As Channel Nine’s “Weekend Today” programme was scheduled to go live on air, the show’s presenters were forced to turn to Twitter to explain their absence.

We Live Security
APRIL 1, 2021
Does every device in your home really need to be connected to the internet? And could your smart appliance be turned against you? The post Is your dishwasher trying to kill you? appeared first on WeLiveSecurity.

Tech Republic Security
MARCH 31, 2021
Most of the recent credential phishing attacks seen by Menlo Security served phony Outlook and Office 365 login pages.

Bleeping Computer
APRIL 1, 2021
Networking device maker Ubiquiti has confirmed that it was the target of an extortion attempt following a January security breach, as revealed by a whistleblower earlier this week. [.].

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

The Hacker News
MARCH 31, 2021
Cybersecurity researchers on Tuesday disclosed details of a sophisticated campaign that deploys malicious backdoors for the purpose of exfiltrating information from a number of industry sectors located in Japan.

Graham Cluley
MARCH 28, 2021
UK fashion retailer FatFace, which made headlines this week by appearing to ask its customers to keep its cyber attack “strictly private and confidential”, has reportedly paid a $2 million ransom to the criminals responsible.

Tech Republic Security
MARCH 31, 2021
Malware is being hidden in seemingly legitimate files that gamers download to install cheat codes or modifications, says Cisco Talos.

Bleeping Computer
MARCH 28, 2021
American managed service provider CompuCom is expecting losses of over $20 million following this month's DarkSide ransomware attack that took down most of its systems. [.].

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Security Boulevard
MARCH 27, 2021
The best way to avoid paying ransom to cyber criminals is to implement security measures in the first place! As mentioned in my. The post A CISO’s Guide to Prevent Ransomware Attacks appeared first on Kratikal Blog. The post A CISO’s Guide to Prevent Ransomware Attacks appeared first on Security Boulevard.

Graham Cluley
APRIL 1, 2021
CISA, the US Department of Homeland Security's Cybersecurity and Infrastructure Security Agency, has told federal agencies that they have until 1April 5 to scan their networks for evidence of intrusion by hackers, and report back the results. Read more in my article on the Tripwire State of Security blog.
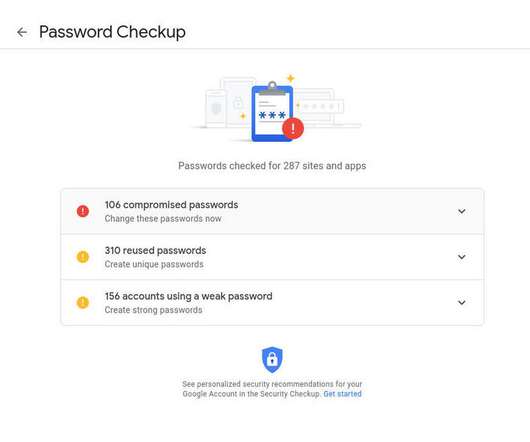
Tech Republic Security
MARCH 31, 2021
Google offers a password checking service that will check all of your Chrome-saved passwords for weaknesses and against known breaches. Jack Wallen shows you how to use this tool.

Bleeping Computer
APRIL 1, 2021
The data breach report from Ubiquiti in January is allegedly a cover-up of a massive incident that put at risk customer data and devices deployed on corporate and home networks. [.].

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

SecureList
MARCH 30, 2021
Why is the campaign called A41APT? In 2019, we observed an APT campaign targeting multiple industries, including the Japanese manufacturing industry and its overseas operations, that was designed to steal information. We named the campaign A41APT (not APT41) which is derived from the host name “DESKTOP-A41UVJV” from the attacker’s system used in the initial infection.

CyberSecurity Insiders
MARCH 31, 2021
This article originally appeared in a global white paper examining the issues around vaccination certificates and immunity passports, and released by Reconnaissance International during the Digital Documents Security virtual event. As vaccination programmes gather momentum, attention is turning towards restoring individual freedoms and reviving economies.

Tech Republic Security
APRIL 1, 2021
Firefox's new feature automatically redirects from HTTP to HTTPS and should be considered a must-use for the security-minded. Jack Wallen explains, and shows you how to enable it.

Bleeping Computer
MARCH 30, 2021
VMware has published security updates to address a high severity vulnerability in vRealize Operations that could allow attackers to steal admin credentials after exploiting vulnerable servers. [.].

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content