Sending Spammers to Password Purgatory with Microsoft Power Automate and Cloudflare Workers KV
Troy Hunt
AUGUST 3, 2022
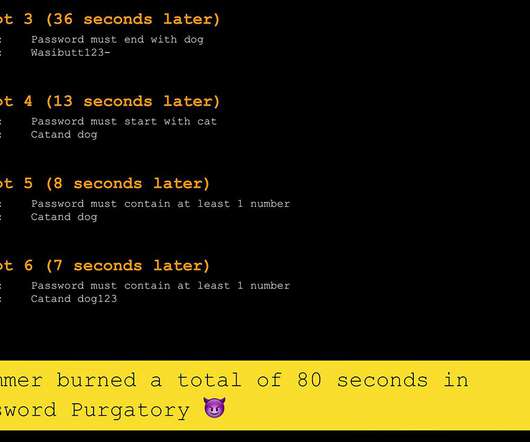
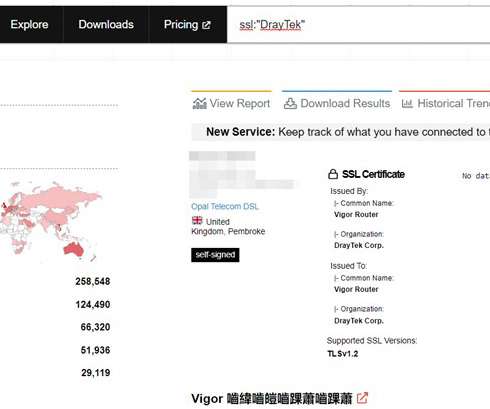
How best to punish spammers? I give this topic a lot of thought because I spend a lot of time sifting through the endless rubbish they send me. And that's when it dawned on me: the punishment should fit the crime - robbing me of my time - which means that I, in turn, need to rob them of their time. With the smallest possible overhead on my time, of course.








































Let's personalize your content