Duo’s Data-Driven Defense: Combatting Cyber Threats in Higher Education
Duo's Security Blog
MAY 30, 2024
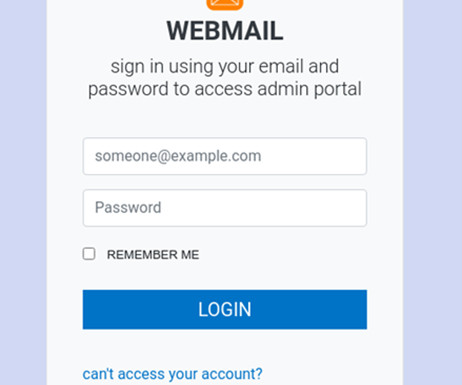
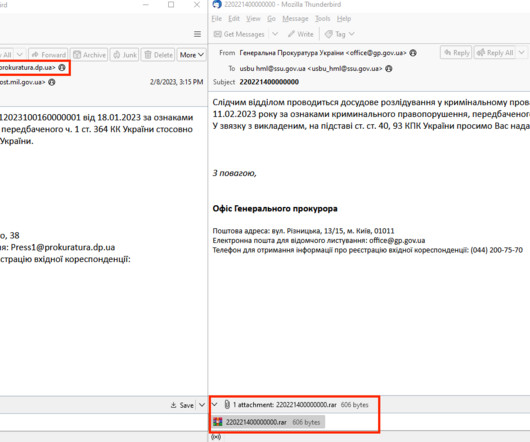
Duo has a long history of protecting students across universities and higher education institutions. Because Duo has such a large presence in the world of education, we can also spot trends in attack tactics and learn how to better secure your organization. But the importance of secure policies should not be ignored.














































Let's personalize your content