Iran-linked DEV-0270 group abuses BitLocker to encrypt victims’ devices
Security Affairs
SEPTEMBER 9, 2022
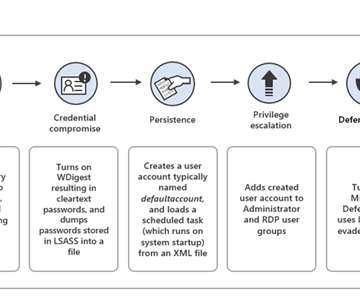
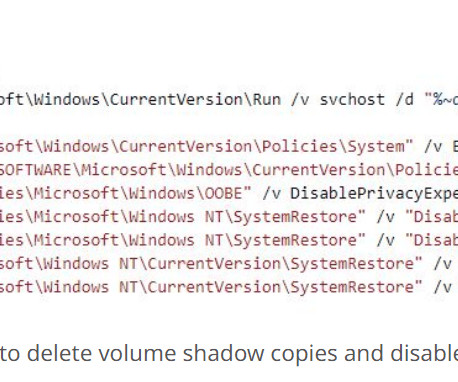
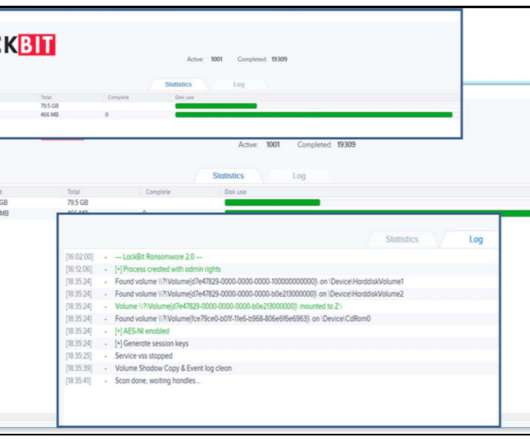
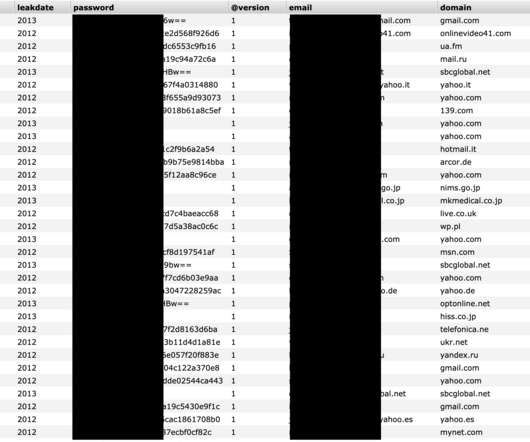
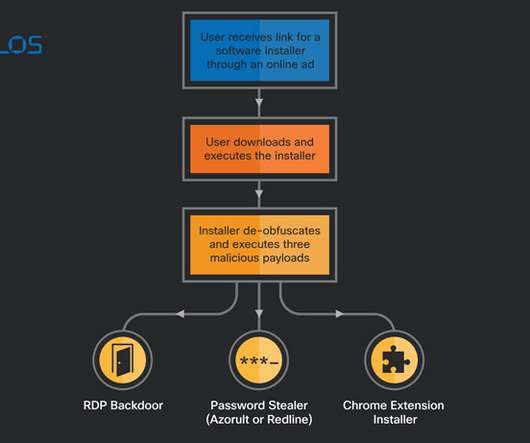
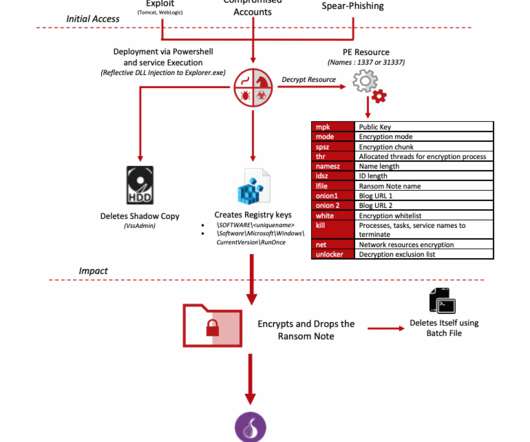
Iran-linked APT group DEV-0270 (aka Nemesis Kitten) is abusing the BitLocker Windows feature to encrypt victims’ devices. Microsoft Security Threat Intelligence researchers reported that Iran-linked APT group DEV-0270 ( Nemesis Kitten ) has been abusing the BitLocker Windows feature to encrypt victims’ devices.











































Let's personalize your content