Akira ransomware gang spotted targeting Cisco VPN products to hack organizations
Security Affairs
AUGUST 22, 2023
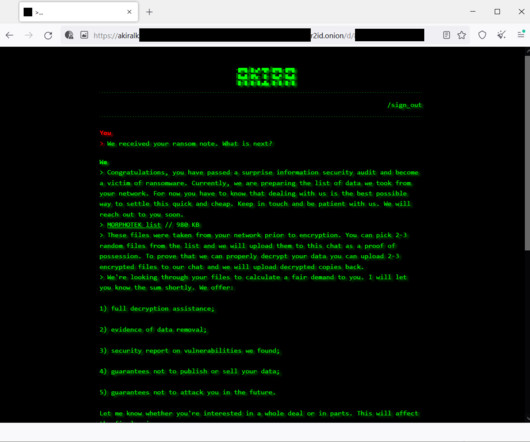
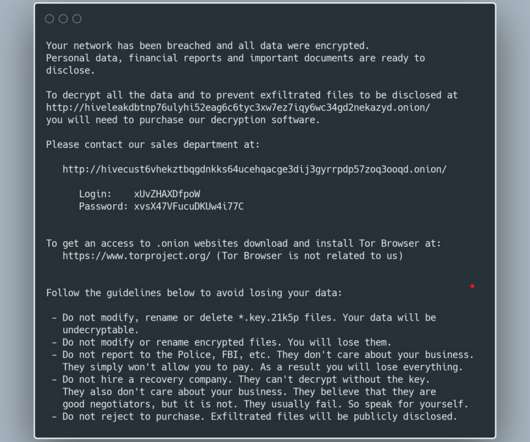
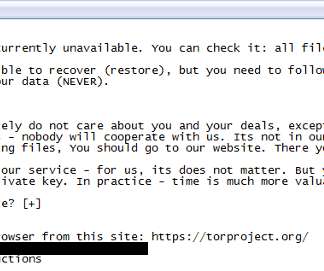
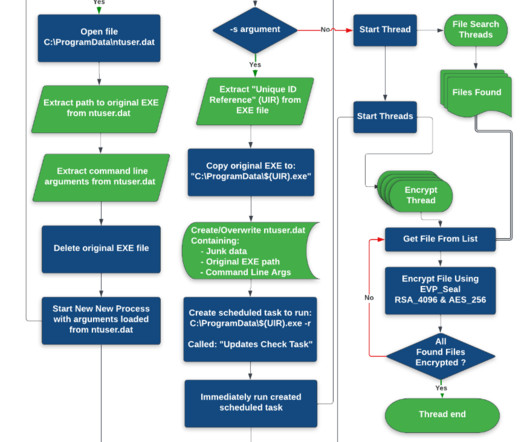
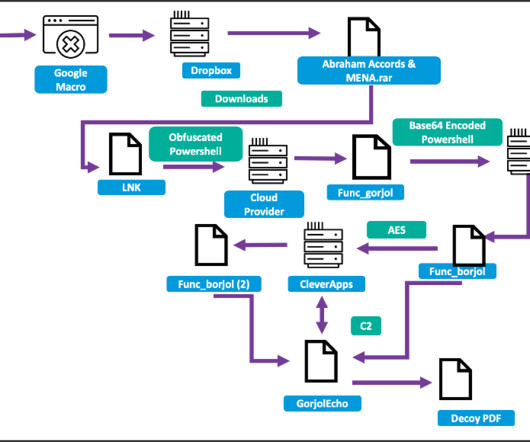
The Akira ransomware gang targets Cisco VPN products to gain initial access to corporate networks and steal their data. The Akira ransomware has been active since March 2023, the threat actors behind the malware claim to have already hacked multiple organizations in multiple industries, including education, finance, and real estate.


































Let's personalize your content