Double-Encrypting Ransomware
Schneier on Security
MAY 21, 2021
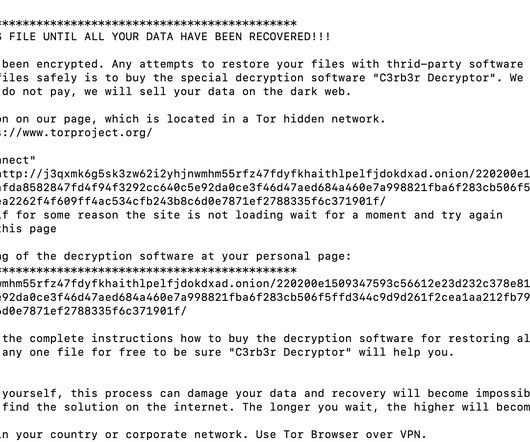
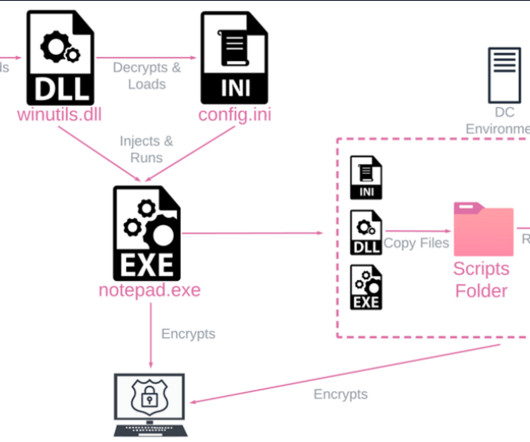
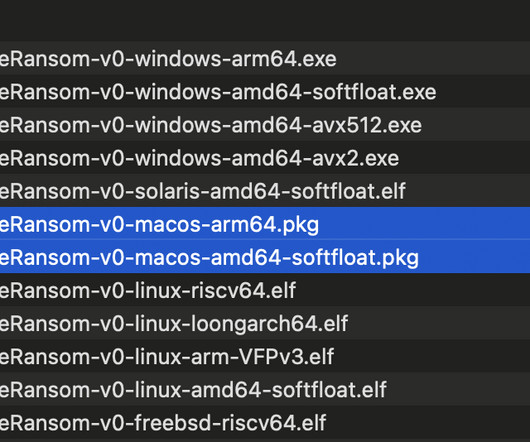
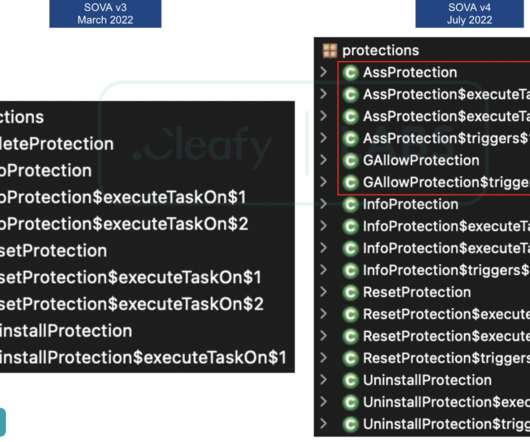
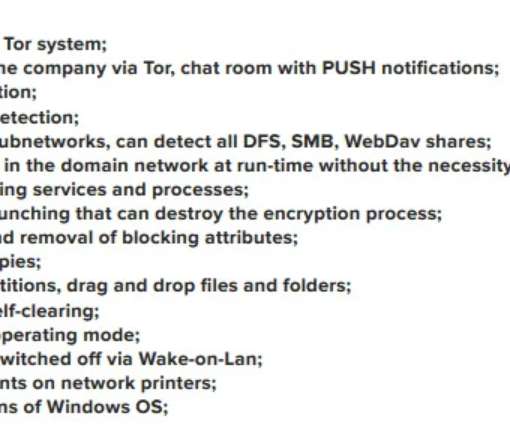
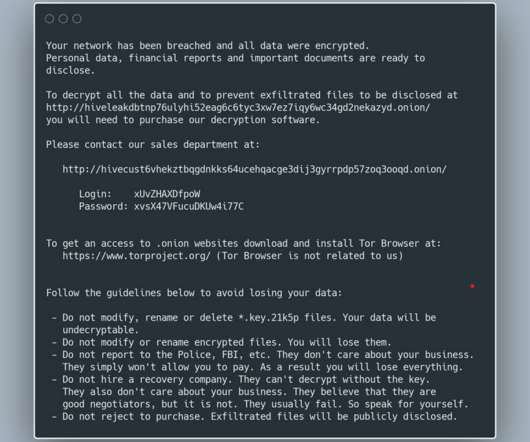
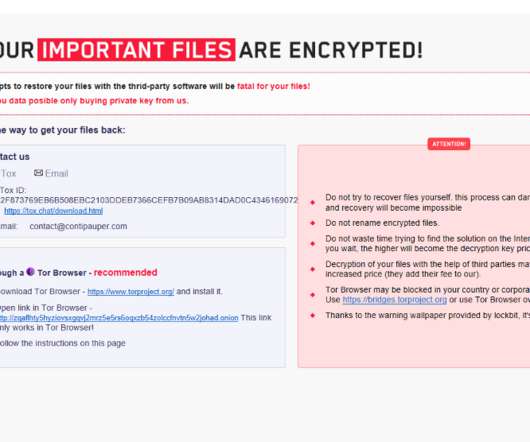
In the first, hackers encrypt data with ransomware A and then re-encrypt that data with ransomware B. The other path involves what Emsisoft calls a “side-by-side encryption” attack, in which attacks encrypt some of an organization’s systems with ransomware A and others with ransomware B.






































Let's personalize your content