Threat Spotlight: Credential Theft vs. Admin Control—Two Devastating Paths to VPN Exploitation
Digital Shadows
MARCH 17, 2025
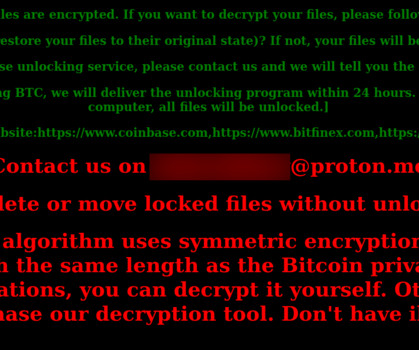
Key Findings Even years after their disclosure, VPN-related vulnerabilities like CVE-2018-13379 and CVE-2022-40684 remain essential tools for attackers, driving large-scale campaigns of credential theft and administrative control. How AI and automation are amplifying the scale and sophistication of VPN attacks.
















































Let's personalize your content