How to Lose a Fortune with Just One Bad Click
Krebs on Security
DECEMBER 18, 2024
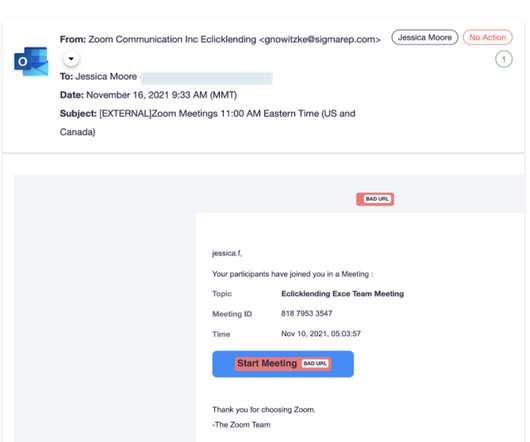
Then came another call, this one allegedly from security personnel at Trezor , a company that makes encrypted hardware devices made to store cryptocurrency seed phrases securely offline. “No one gets arrested,” Daniel enthused to Junseth in the May 7 podcast, which quickly went viral on social media.















































Let's personalize your content