Interpol arrests 2000 criminals launching social engineering attacks
CyberSecurity Insiders
JUNE 17, 2022
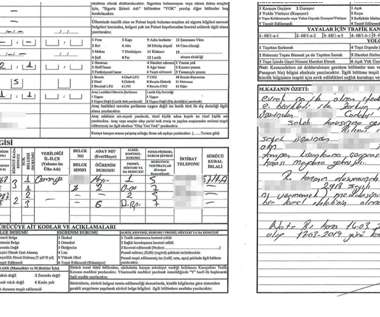
In what appears as an operation first of its kind, Interpol has arrested over 2000 criminals who launched social engineering attacks worldwide. As the IT working community followed a strict Work From Home(WFH) culture, there has been a rise in the number of internet scams. More details about the scam will be updated shortly! .


















































Let's personalize your content