Who’s Behind the ‘Web Listings’ Mail Scam?
Krebs on Security
MARCH 23, 2020
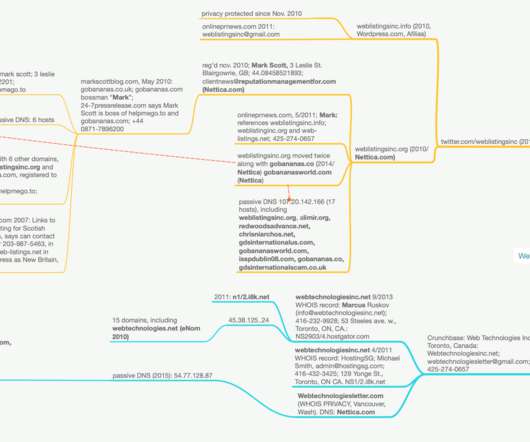
political campaigns, cities and towns had paid a shady company called Web Listings Inc. after receiving what looked like a bill for search engine optimization (SEO) services rendered on behalf of their domain names. Since at least 2007, Web Listings Inc. In December 2018, KrebsOnSecurity looked at how dozens of U.S.



















Let's personalize your content