Palo Alto Firewalls Under Attack: Critical Flaw Exploited to Deploy Cryptojacking Malware
Penetration Testing
APRIL 28, 2024
Palo Alto Networks’ popular firewall appliances are currently in the crosshairs of cybercriminals.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Penetration Testing
APRIL 28, 2024
Palo Alto Networks’ popular firewall appliances are currently in the crosshairs of cybercriminals.

Penetration Testing
MARCH 12, 2024
Security researcher ‘stealthcopter‘ has exposed a severe security hole in the widely used WordPress Anti-Malware Security and Brute-Force Firewall plugin (GOTMLS). This vulnerability, labeled CVE-2024-22144 with a “Critical” CVSS score of 9.0,
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Penetration Testing
FEBRUARY 10, 2024
A new menace emerged, dubbed “KV-botnet,” this sophisticated malware network was identified by Lumen’s Black Lotus Labs, revealing a covert operation that had infected small-office and home-office routers and firewall devices globally.

eSecurity Planet
FEBRUARY 21, 2024
A firewall audit is a procedure for reviewing and reconfiguring firewalls as needed so they still suit your organization’s security goals. Auditing your firewall is one of the most important steps to ensuring it’s still equipped to protect the perimeter of your business’ network.

eSecurity Planet
APRIL 30, 2024
Setting up a firewall is the first step in securing your network. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively improve your network integrity and data security. Verify that the chosen firewall can meet your security standards and functions.

CyberSecurity Insiders
MAY 28, 2023
Malware Analysis: Explore malware types, their behavior, and the techniques used for analyzing and detecting them. Investigate malware’s propagation methods, evasion techniques, and methods for identifying and mitigating potential threats.

SiteLock
OCTOBER 21, 2021
Let us start with the abbreviations that define the categories of information security products: WAF stands for Web Application Firewall , NGFW stands for Next Generation Firewall. NGFW (or Next Generation Firewall) is an evolution of traditional firewalls and serves to delimit access between network segments.

SiteLock
AUGUST 27, 2021
A recent report from PandaLabs suggests that “there were twice as many malware infections in 2014 compared to 2013” and that 2015 could be even worse. Today’s attacks are becoming increasingly sophisticated, and a simple malware injection can compromise your entire database. Automatic remediation of known threats.

Krebs on Security
MARCH 2, 2020
A large number of French critical infrastructure firms were hacked as part of an extended malware campaign that appears to have been orchestrated by at least one attacker based in Morocco, KrebsOnSecurity has learned.

Security Affairs
JANUARY 28, 2023
One of the most recent attacks was reported by Computerland in Belgium against SMBs in the country, but according to the company they were targeted by a group of cybercriminals who appeared to be using a variant of the LockBit locker malware.

eSecurity Planet
JUNE 20, 2023
After surveying trusted penetration testing sources and published pricing, the cost of a penetration test for the average organization is $18,300. and different types of penetration tests (black box, gray box, white box, social engineering, etc.).

Security Affairs
NOVEMBER 25, 2020
Hackers compromised the company point-of-sale (PoS) systems with malware that was designed to steal payment card data. . The settlement was announced by Delaware Attorney-General Kathy Jennings this week, it confirmed that 46 states have reached an agreement with the US company. . ” .

eSecurity Planet
APRIL 29, 2024
The problem: Microsoft Threat Intelligence published a report on how a Russian threat group, known as APT28 or Forest Blizzard, used customized malware to exploit the CVE-2022-38028 vulnerability in the Windows Print Spooler to gain elevated permissions. Attackers can easily exploit 10.0

The Last Watchdog
SEPTEMBER 4, 2018
Spirent refers to this as “data breach emulation,’’ something David DeSanto, Spirent’s threat research director, told me is designed to give companyies a great advantage; it makes it possible to see precisely how the latest ransomware or crypto mining malware would impact a specific network, with all of its quirky complexity. DeSanto: Yes.

Zigrin Security
OCTOBER 11, 2023
For a detailed threat actor description do not forget to check out our blog article about selecting between black-box, white-box, and grey-box penetration tests and also you would know which pentest you need against a specific threat actor. Regularly conduct cybersecurity training sessions to reinforce good security habits.

Cytelligence
NOVEMBER 16, 2023
Here are some key areas to consider: Network Defense Implement network segmentation, firewall rules, and intrusion detection systems (IDS) to protect against unauthorized access and lateral movement within the network. Implement secure coding practices and web application firewalls (WAFs) to protect against web-based attacks.

eSecurity Planet
FEBRUARY 14, 2023
Virtual patching bypasses the complex and time-consuming process of developing and deploying patches by using rules, mitigations and protective steps, often at the IPS or firewall level, to shore up networks to prevent attackers or malware from accessing these vulnerabilities. Proactive identification approaches are recommended.

Cisco Security
OCTOBER 26, 2022
Commodity malware, such as the Qakbot banking trojan, was observed in multiple engagements this quarter. The malware operators behind Raccoon introduced new functionality to the malware at the end of June, which likely contributed to its increased presence in engagements this quarter. .

SecureWorld News
OCTOBER 22, 2023
Enforce enterprise-grade antivirus, firewalls, and internet security software across all connected devices. Document how security incidents like data breaches, insider threats, phishing attacks, DDoS (distributed denial-of-service), and malware infections will be reported, contained, and reported on.
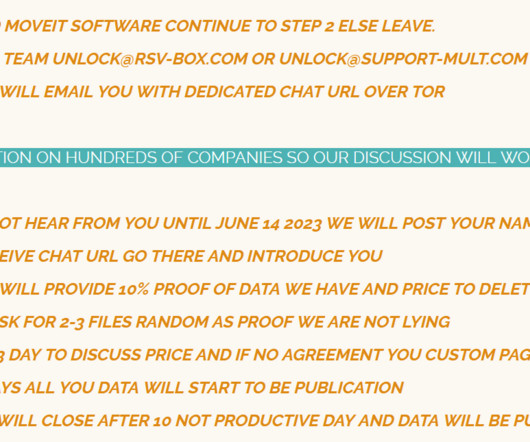
Security Affairs
JUNE 16, 2023
Customers have to modify firewall rules to deny HTTP and HTTPs traffic to the software on ports 80 and 443. WE ALSO WANT TO REMIND ALL COMPANY THAT IF YOU PUT DATA ON INTERNET WHERE DATA IS NOT PROTECT DO NOT BLAME US FOR PENETRATION TESTING SERVICE. Disable all HTTP and HTTPs traffic to your MOVEit Transfer environment.

eSecurity Planet
NOVEMBER 18, 2021
Most operations use payloads, but there are a few payload-less attacks, such as phishing campaigns that do not include malicious links or malware , but rely on more sophisticated deception such as spoofing to trick their targets. Even if there’s a firewall enabled, it won’t block outgoing TCP connections. How Payloads Get Executed.

Security Affairs
JUNE 5, 2019
BlueKeep is a wormable flaw that can be exploited by malware authors to create malicious code with WannaCry capabilities. osum0x0 announced to have has developed a module for the popular Metasploit penetration testing framework to exploit the critical BlueKeep flaw. A few hours ago, th e esecurity researcher Z??osum0x0

Herjavec Group
MAY 19, 2022
No matter how many firewalls or network controls you have in place, the risk of insider threat will always be present. Segment your internal corporate networks to isolate any malware infections that may arise. Conduct regular social engineering tests on your employees to actively demonstrate where improvements need to be made.

NopSec
AUGUST 16, 2022
Individuals can use a configuration review scanner and authenticated scans to monitor the security of their operating systems automatically and make sure they aren’t affected by malware. Critical Security Control 8: Audit Log Management This control refers to audit logs for firewalls, network devices, servers, and hosts.

SiteLock
AUGUST 27, 2021
The SiteLock TrueShield web application firewall stops SQL injection attacks before they reach your site. SiteLock SMART and penetration testing scanners find and remove malware automatically if by some chance malware gets on your site.

Security Affairs
AUGUST 20, 2018
The popular malware researchers Marco Ramilli has analyzed a malware that remained under the radar for more than two years. The first thought that you might have as an experienced malware reverse engineer would be: “Ok, another bytecode reversing night, easy. Resource (a.k.a package in where it will be contextualized).

SecureWorld News
DECEMBER 1, 2020
In 2014, hackers accessed the company's network and installed malware to the self-checkout point-of-sale system. It has also agreed to strengthen its information security program through a series of steps, which must be done within 180 days of the agreement. The Home Depot data breach and agreement.

Malwarebytes
MAY 23, 2023
Cobalt Strike is a commercial penetration testing software suite. Common tools for data exfiltration include Rclone, Rsync, various web-based file storage services (also used by threat actors to implant malware/tools on the affected network), and FTP/SFTP. Signs of the presence of Cobalt Strike beacon/client. Prevent intrusions.

SiteLock
AUGUST 27, 2021
Use a website scanner that will automatically remove website malware from your site files as soon as its infected. Implement a web application firewall (WAF) to block cybercriminals and bad bots from accessing your website. Invest in a professional penetration testing service. Website Security Tips.

Herjavec Group
MARCH 24, 2022
Internet-facing architecture that is being ASV scanned has grown more complex over the last years with the implementation of HTTPS load balancers, web application firewalls, deep packet inspection capable intrusion detection/prevention (IDS/IPS) systems, and next-gen firewalls. Client-Side Web Browser Vulnerabilities.

eSecurity Planet
SEPTEMBER 10, 2021
What are the results of the provider’s most recent penetration tests? A defense-in-depth strategy that includes firewalls, anti-malware, intrusion detection, and access control has long been the standard for endpoint security. Conduct audits and penetration testing. Enable security logs.

Security Affairs
APRIL 5, 2019
Malware researcher and founder of Yoroi Marco Ramill described a step-by-step procedure that shows how to dissect an Office dropper. Both of those tricks are quite well-known in the malware industry. From here you might decide to extract the dropper websites and block them on your firewall/proxy/etc.

eSecurity Planet
JUNE 21, 2022
The certification covers active defense, defense in depth, access control, cryptography, defensible network architecture and network security, incident handling and response, vulnerability scanning and penetration testing, security policy, IT risk management, virtualization and cloud security , and Windows and Linux security.

eSecurity Planet
OCTOBER 20, 2022
Provider Services & Software: Cloud providers may offer a range of services such as databases, firewalls , artificial intelligence (AI) tools, and application programming interface (API) connections. Network, firewall, and web application firewall (WAF) hardening. Network, API, firewall, and WAF hardening.

CyberSecurity Insiders
JANUARY 18, 2022
The same symptoms will occur in your IT environment as the malware spreads downloading data and expanding across your global network corrupting backups and leaving little options. Run external and internal penetration tests to see if any holes exist and quickly execute remediation plans. Instead, they will use traditional mail.

SecureWorld News
APRIL 17, 2022
It was once the case that cybersecurity technology consisted of little more than a firewall and antivirus software. There are tasks such as penetration testing. It can certainly be said that advances in technology have had a huge impact on cybersecurity in recent years.

The Last Watchdog
APRIL 30, 2020
Hacking groups today routinely do this; they cover their tracks by injecting malicious code well beneath the purview of legacy firewalls, intrusion detection tools and data loss prevention systems. What Virsec is bringing to the DevSecOps table is, essentially, very granular penetration testing based on in-the-field forensics.

eSecurity Planet
MARCH 17, 2023
Encryption Product Guides Top 10 Full Disk Encryption Software Products 15 Best Encryption Software & Tools Breach and Attack Simulation (BAS) Breach and attack simulation (BAS) solutions share some similarities with vulnerability management and penetration testing solutions.

eSecurity Planet
SEPTEMBER 10, 2021
The following sections speak to how ransomware can affect organizations with backup strategies in place, the implications of advanced malware , and why the type of backup solution matters. Malware constantly evolves to match advancing cybersecurity standards and solutions, and ransomware is no exception. Data Exfiltration.

NopSec
JULY 18, 2017
Web application security testing could determine the effectiveness of Web Application Firewall guarding Internet-facing applications. Web browsers most common vulnerabilities and missing patches are reported. Dynamic Analysis OWASP Top 10 vulnerabilities, including SQLi, XSS, CSRF, path traversal, etc.

eSecurity Planet
AUGUST 22, 2023
Be Thorough It is all too easy in an attack to find the apparent source of malware, eradicate it and leave it at that. When your systems have been breached by malware or another threat, using sophisticated security tools to find any lingering code or files is important. But you may miss further traces of it on other systems.

Zigrin Security
JUNE 28, 2023
Malware distribution: Attackers can inject malicious scripts that redirect users to websites hosting malware, leading to the installation of harmful software on their systems. Protecting Your Site from Reflected XSS Attacks To protect your site from reflected XSS attacks, it is essential to implement proper output sanitization.

eSecurity Planet
MARCH 14, 2023
When the internet arrived, the network added a firewall to protect networks and users as they connected to the world wide web. Technical controls may be implemented by: Hardware appliances : switches, routers, firewalls, etc. In a complex, modern network, this assumption falls apart.

NopSec
AUGUST 2, 2017
Antivirus software is one of the oldest and the most ever present security control against malware and various types of malicious software. It’s historically focused on blocking viruses, then eventually evolved into blocking all sort of other malware. “I I have antivirus so I’m covered” used have some legitimate weight to it.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content