Australian man charged with creating and selling the Imminent Monitor spyware
Security Affairs
AUGUST 1, 2022
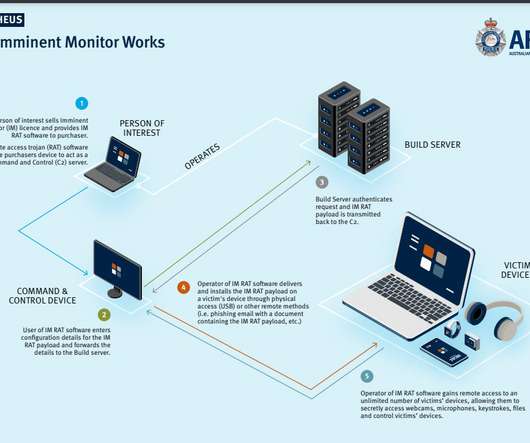
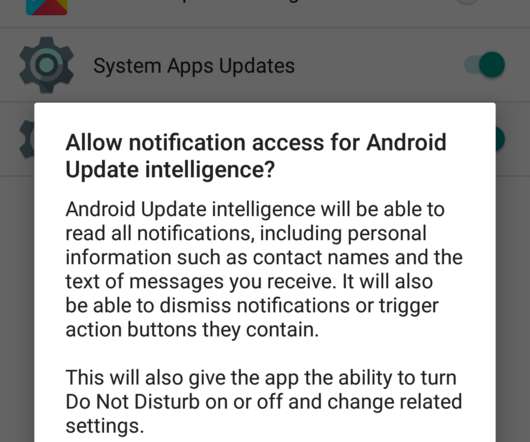
An Australian national has been charged for the creation and sale of the Imminent Monitor (IM) spyware, which was also used for criminal purposes. The 24-year-old Australian national Jacob Wayne John Keen has been charged for his alleged role in the development and sale of spyware known as Imminent Monitor (IM).






















Let's personalize your content