Stealth Soldier backdoor used is targeted espionage attacks in Libya
Security Affairs
JUNE 9, 2023
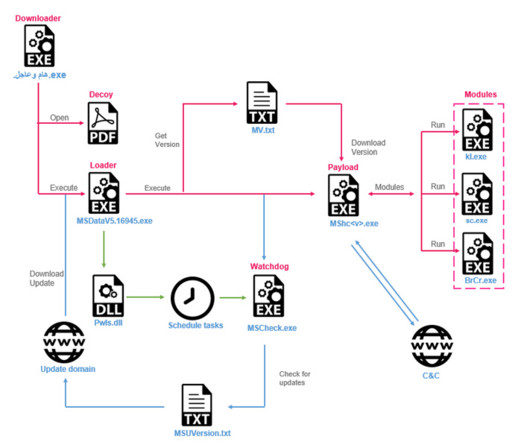
Stealth Soldier is surveillance software that allows operators to spy on the victims and exfiltrate collected data. “Stealth Soldier malware is an undocumented backdoor that primarily operates surveillance functions such as file exfiltration, screen and microphone recording, keystroke logging and stealing browser information.”


















Let's personalize your content