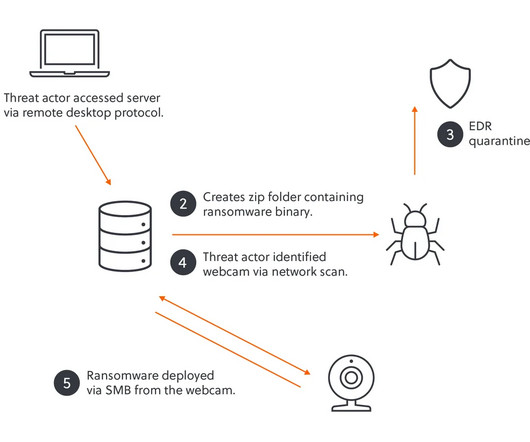
Akira ransomware gang used an unsecured webcam to bypass EDR
Security Affairs
MARCH 8, 2025
They found unsecured IoT devices, including webcams and a fingerprint scanner, using them to bypass security defenses and successfully deploy the ransomware. The IoT device was running a lightweight Linux OS, that was the perfect target for Akiras Linux ransomware variant. ” concludes the report.











































Let's personalize your content