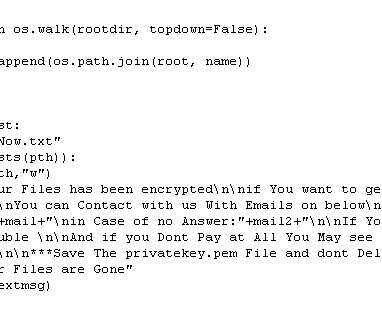
Hackers are actively exploiting CVE-2022-47966 flaw in Zoho ManageEngine
Security Affairs
FEBRUARY 24, 2023
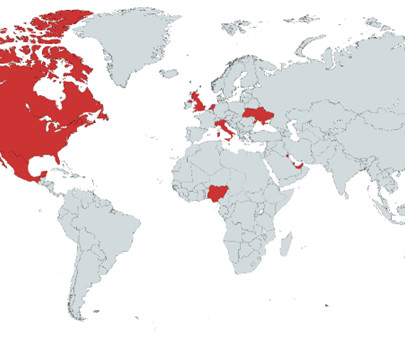
The issue affects tens of products, including Access Manager Plus, ADManager Plus, Password Manager Pro, Remote Access Plus, and Remote Monitoring and Management (RMM). The analysis of the experts revealed 2,000 to 4,000 servers accessible from the Internet. and the U.S.






















Let's personalize your content