Processing 23 Billion Rows of ALIEN TXTBASE Stealer Logs
Troy Hunt
FEBRUARY 25, 2025
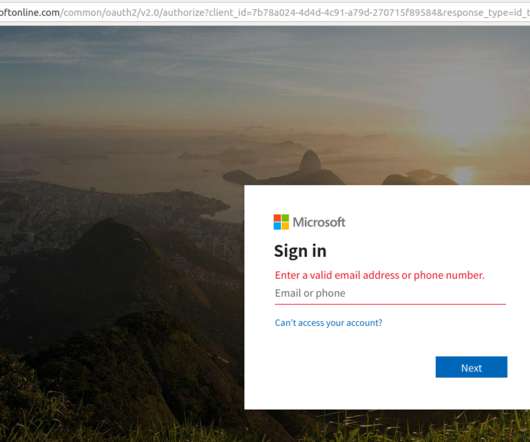
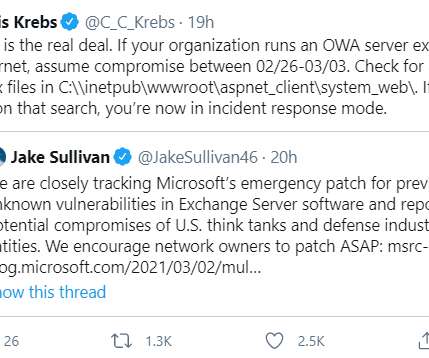
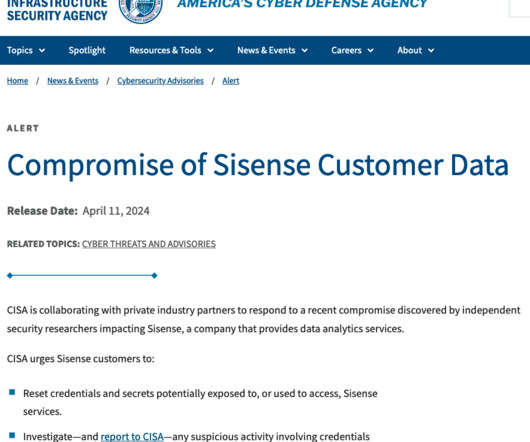
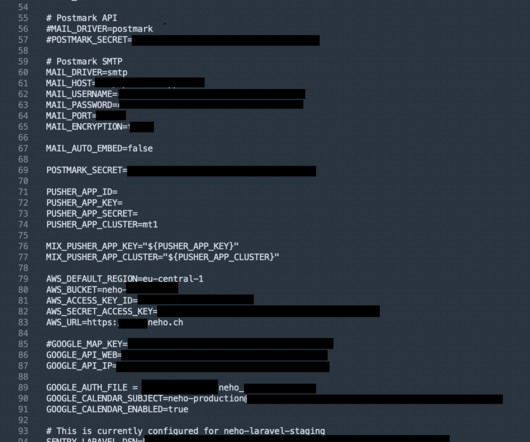
We've also added 244M passwords we've never seen before to Pwned Passwords and updated the counts against another 199M that were already in there. The file in the image above contained over 36 million rows of data consisting of website URLs and the email addresses and passwords entered into them.








































Let's personalize your content