Down the Cloudflare / Stripe / OWASP Rabbit Hole: A Tale of 6 Rabbits Deep ? ? ? ? ? ?
Troy Hunt
FEBRUARY 19, 2023
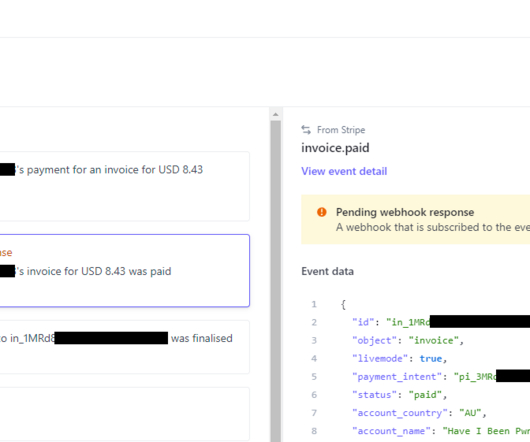
I love Stripe, it's such an awesome service that abstracts away so much pain and it's dead simple to integrate via their various APIs. It's also dead simple to configure Stripe to send notices back to your own service via webhooks. When that call doesn't happen, well, let's go down the first rabbit hole.


















































Let's personalize your content