Sudanese Brothers Arrested in ‘AnonSudan’ Takedown
Krebs on Security
OCTOBER 17, 2024
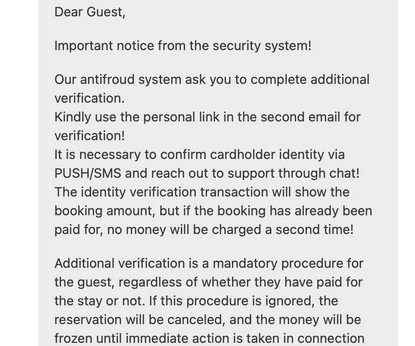
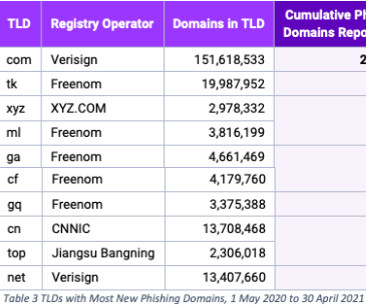
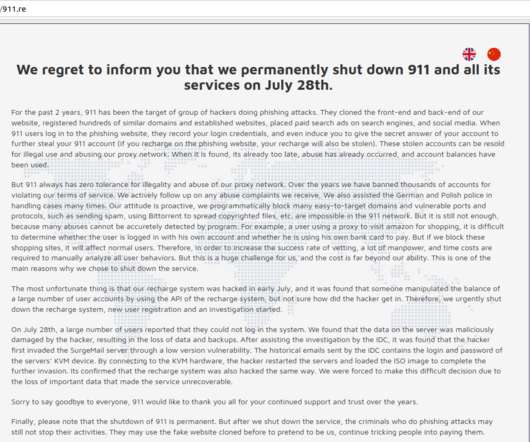
Image: FBI Active since at least January 2023, AnonSudan has been described in media reports as a “hacktivist” group motivated by ideological causes. The younger brother is facing charges that could land him life in prison for allegedly seeking to kill people with his attacks.



































Let's personalize your content