GUEST ESSAY: A roadmap to achieve a better balance of network security and performance
The Last Watchdog
OCTOBER 31, 2022
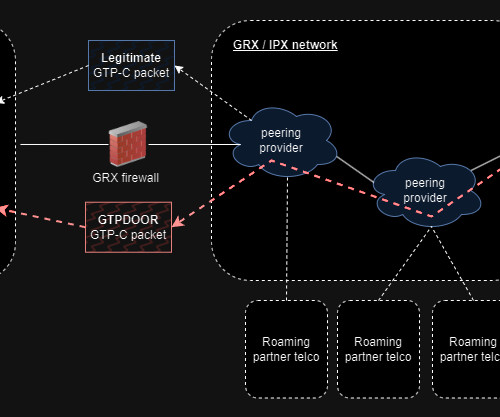
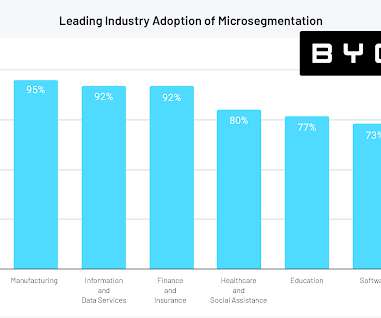
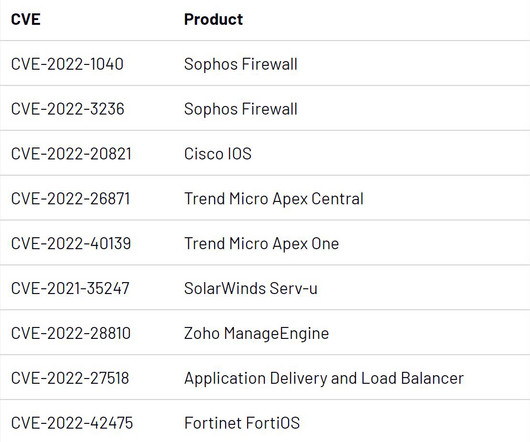
But there’s something you can do to get better at striking it: build that balance into your network testing and policy management. Why do so many businesses struggle to balance network security and user experience? Your network security simulations should do the same. Navigating threats. Test and test again.











































Let's personalize your content