Best Wi-Fi Security & Performance Testing Tools for 2022
eSecurity Planet
MAY 20, 2022
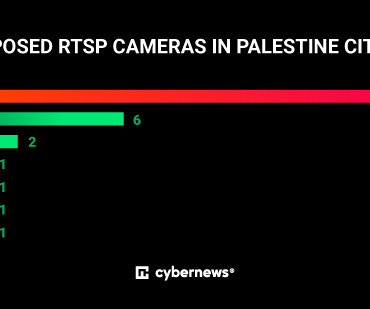
With other vulnerabilities such as sharing devices and Wi-Fi access with family members or lax password hygiene, security becomes a real challenge. To catch them, administration policies on continuous surveillance and periodic assessments should be in place. The discovered wireless packets can be imported into Wireshark and TCPdump.















Let's personalize your content