Ransomware: The Types of and How to Make Ransomware?
Hacker Combat
FEBRUARY 28, 2021
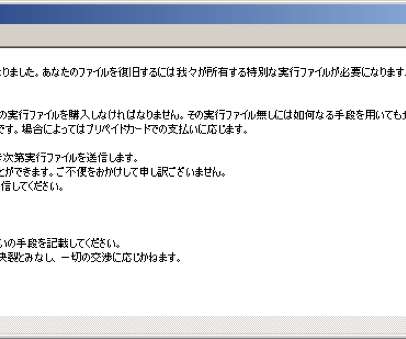
How to Make Ransomware? Ransomware is a type of malware that operates by either locking you out of your computer or mobile device or by manipulating your files in such a way that you cannot access nor utilize them. Types of Ransomware. Ransomware is classified into two. Crypto ransomware.















































Let's personalize your content